Amazon VPC (Virtual Private Cloud) is like your own private data center inside the AWS cloud. It lets you launch servers (EC2 instances) in an isolated, secure network that you fully control.
Within a VPC, you can:
- Create public or private subnets,
- Set access rules using security groups and network ACLs,
- Control IP addresses, route tables, and internet gateways,
- Decide whether your servers connect to the internet or stay private.
It is a customizable and secure environment to run your applications, databases, and services just like building your own network inside the cloud.
Example
Let’s try to understand it by taking an example of the Codezaza office setup. Just like GeeksforGeeks carefully organizes its departments and controls access, a VPC organizes and secures resources in the AWS cloud.
- The entire Codezaza office building = VPC (a private space where everything is managed securely)
- Different departments like Editorial, Development, HR = Subnets (some open for external interaction, some private for internal work)
- Security guards at every gate = Security Groups and Firewalls (deciding who can enter or leave)
- The internet connection for employees and visitors = Internet Gateway (allowing public access where needed)
- Private tunnels connecting to partner companies = VPN or Direct Connect (secure, private connections to other trusted networks)
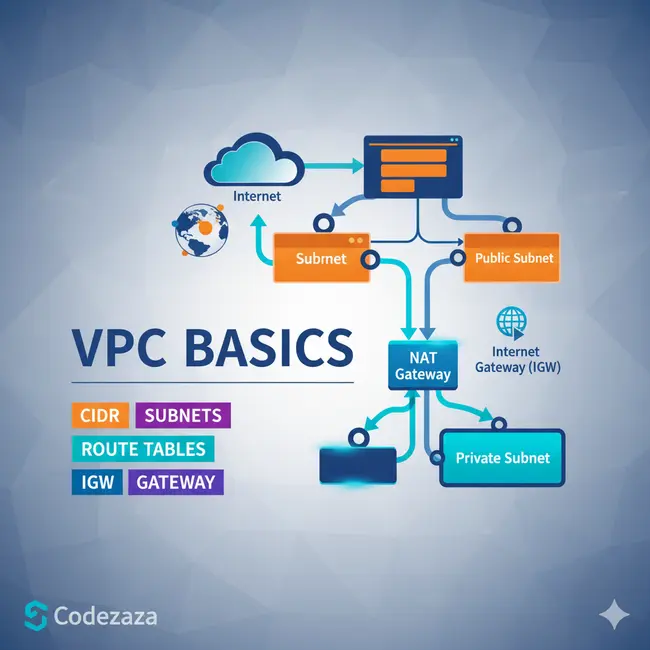
Amazon VPC Architecture
The basic architecture of a properly functioning VPC consists of many distinct services such as Gateway, Load Balancer, Subnets, etc. Altogether, these resources are clubbed under a VPC to create an isolated virtual environment. Along with these services, there are also security checks on multiple levels.
It is initially divided into subnets, connected with each other via route tables along with a load balancer.
Core Components of Amazon VPC
1. Virtual Private Cloud (VPC)
You can launch AWS resources into a defined virtual network using Amazon Virtual Private Cloud (Amazon VPC). With the advantages of utilizing the scalable infrastructure of AWS, this virtual network closely mimics a conventional network that you would operate in your own data center. /16 user-defined address space maximum (65,536 addresses)
2. Subnets
Subnets divide your VPC into smaller, separate networks. As a result, they help you organize and secure your resources more effectively.
- Limit: You can create up to 200 subnets in a VPC.
- Types:
- Public Subnets: These connect to the internet, so users can access them.
- Private Subnets: These stay internal, keeping communication private.
- Purpose: By separating networks, subnets improve securitystru security and control traffic.
3. Route Tables
Route Tables are mainly used to Define the protocol for traffic routing between the subnets. They tell data where to go inside your VPC. For example, whether to stay within a private network or head out to the internet.
- Each subnet must be associated with a route table.
- Routes define the direction of traffic based on IP addresses.
4. Network Access Control Lists (NACLs)
Network Access Control Lists (NACL) for VPC serve as a firewall by managing both inbound and outbound rules. There will be a default NACL for each VPC that cannot be deleted
5. Internet Gateway (IGW)
The Internet Gateway (IGW) will make it possible to link the resources in the VPC to the Internet allowing resources like web servers to be accessed publicly. Without an IGW, your VPC cannot communicate with the internet.
6. Network Address Translation (NAT)
A NAT Gateway lets private subnet instances connect to the internet for tasks like downloading updates. However, it blocks incoming connections from the internet to keep those instances secure.
It ensures private resources stay hidden while allowing outbound access.
Amazon VPC
If the subnet has internet access then it is called PublicSubnet.
If the subnet doesn’t have internet access then it is called PrivateSubnet.
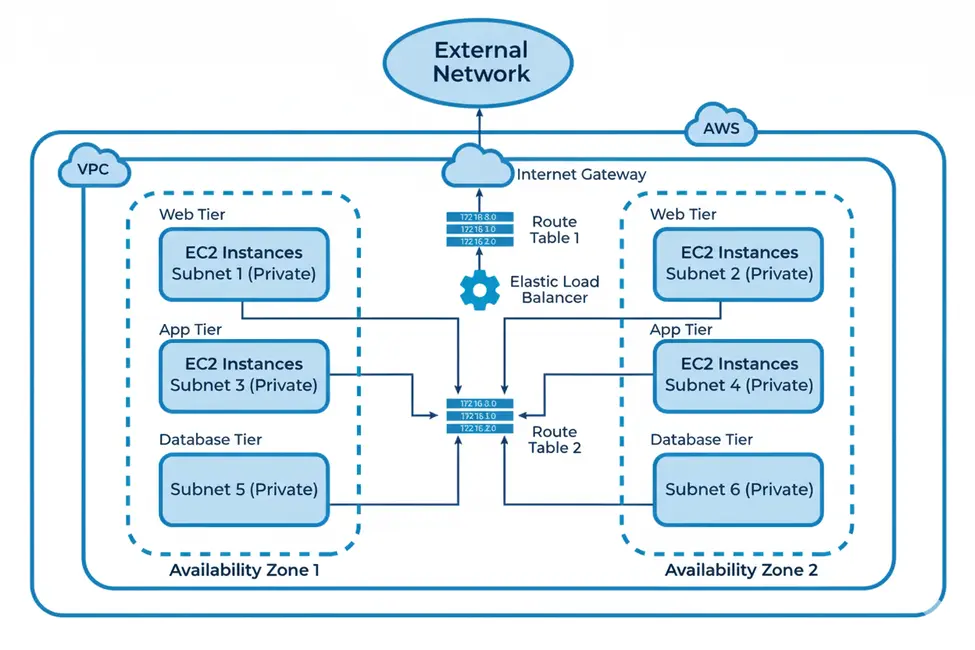
A subnet must reside entirely within one Availability Zone.
An entire subnet must be contained within a single Availability Zone.
Access between instances is managed by VPC Security Groups for both inbound and outgoing traffic (Security Groups support both inbound and outbound rules, but they are stateful, unlike NACLs).
We can specify Subnet IP Routing with the aid of the Route Table.
If a server/instance which is in a private subnet wants to reach the internet then it must have NAT in a public subnet.
Subnets: Public and Private
Subnets split your VPC into smaller networks for better organization and security. For instance, each subnet lives entirely within one Availability Zone, ensuring resources stay isolated.
- Public Subnets: These connect to the internet via an Internet Gateway, allowing public access.
- Private Subnets: These lack internet access, keeping resources internal and secure.
- Key Points:
- You can create up to 200 subnets per VPC.
- Every subnet needs a route table to manage traffic.
- If a private subnet instance, like a server, needs internet access (e.g., for updates), it requires a NAT Gateway in a public subnet.
Route Tables: Directing Network Traffic
Route Tables contain rules, called routes, that guide network traffic in your VPC. Specifically, they decide whether data stays within a private subnet or reaches the internet.
- Key Facts:
- Each subnet must link to a route table.
- You can create multiple route tables in a VPC as needed.
- If a route table has dependencies (e.g., linked subnets), you cannot delete it.
Internet Gateway (IGW): Connecting to the Internet
An Internet Gateway (IGW) allows your VPC resources, like EC2 instances, to access the internet. As a result, public subnets can host web servers accessible to users.
- Key Details:
- A VPC supports only one attached IGW at a time, though you can create multiple IGWs in your AWS account.
- You cannot detach an IGW if resources in the VPC are actively using it.
Network Access Control Lists (NACLs): Your VPC Firewall
NACLs act as a firewall for your VPC, controlling traffic to and from subnets. For example, you can set rules to allow or block specific traffic.
- Default NACL: Every VPC includes a default NACL, automatically linked to default subnets, and you cannot delete it.
- Function: Unlike stateful Security Groups, NACLs are stateless, meaning they evaluate inbound and outbound rules separately.
Security Groups: Managing Instance Access
Security Groups control traffic to and from instances within your VPC. Unlike NACLs, they are stateful, meaning they automatically allow return traffic for approved requests.
- Purpose: They manage both inbound and outbound rules to secure your instances, like EC2 servers.
Classless Inter-Domain Routing (CIDR): Defining IP Ranges
CIDR is a method for assigning IP addresses and routing traffic in your VPC. When you set up a VPC, you specify a CIDR block, such as 10.0.0.0/16, to define its IP range (0–32 bits).
- Purpose: CIDR helps you allocate IP addresses efficiently for your network.
RFC1918 Addresses: Private IP Ranges
RFC1918 addresses are private IP addresses used in internal networks, inaccessible from the public internet. Consequently, they enhance security for your VPC resources.
- RFC1918 Ranges:
- 10.0.0.0–10.255.255.255 (10/8 prefix)
- 172.16.0.0–172.31.255.255 (172.16/12 prefix)
- 192.168.0.0–192.168.255.255 (192.168/16 prefix)
- Use Case: Enterprises assign these addresses to internal hosts, like servers, for secure communication.
Conclusion:
Amazon Virtual Private Cloud (VPC) empowers you to create a secure and flexible network in the AWS cloud. By understanding its core components, you can build a robust network tailored to your needs. Specifically, CIDR blocks define your VPC’s IP address range, enabling efficient IP management. Meanwhile, subnets organize resources into public or private segments, enhancing security and control. Additionally, Route Tables direct traffic flow, ensuring data reaches the right destination. Furthermore, the Internet Gateway (IGW) connects public subnets to the internet, while NAT Gateways allow private subnets to access the internet securely without exposing resources. Together, these elements provide a powerful framework for managing cloud networks. Therefore, mastering CIDR, subnets, Route Tables, IGW, and NAT equips you to design secure, scalable, and efficient VPCs for any application.