Amazon Route 53 Resolver DNS Firewall helps you control access to domain names and block DNS-level threats for queries leaving your VPC through the Route 53 Resolver. It provides a powerful way to secure DNS traffic at scale, without adding extra infrastructure.
With DNS Firewall, you can create domain filtering rules organized into rule groups. These rule groups are then associated with your VPCs. Using these rules, you can:
Fine-tune rule behavior to allow specific query types (for example, MX records) while still blocking others.
Block or allow specific domain names.
Use advanced rules to protect against DNS tunneling and Domain Generation Algorithm (DGA)-based threats.
Customize responses for blocked DNS queries.
Key Components of Route 53 Resolver DNS Firewall
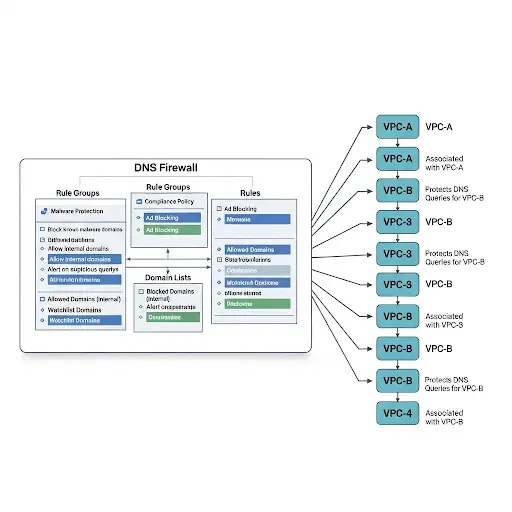
1. DNS Firewall Rule Group
A DNS Firewall rule group is essentially a container that holds multiple DNS filtering rules. It acts as a reusable collection that can be associated with one or more Virtual Private Clouds (VPCs). Once a rule group is linked to a VPC, DNS Firewall filtering becomes active for that VPC. This means every DNS query from that VPC is passed through the associated rules before being resolved. If you associate multiple rule groups with the same VPC, the rules are processed in order of priority. The lowest numeric value has the highest precedence, ensuring that the most critical filtering rules are applied first.
2. DNS Firewall Rule
A DNS Firewall rule defines how a specific DNS query should be handled. Rules are always part of a rule group and cannot exist independently. Each rule can be based on either a domain list (which specifies domains to allow or block) or an advanced protection setting (which detects DNS tunneling or Domain Generation Algorithm threats). Using these rules, administrators can allow, block, or trigger alerts for suspicious queries. Additionally, rules can be applied to specific query types, such as MX records, giving fine-grained control. Rules also support custom responses, which means you can configure the type of reply DNS Firewall returns for blocked queries. The execution order of rules within a rule group is determined by their priority, starting from the lowest number.
3. Domain List
A domain list is a named set of domains that DNS Firewall uses when evaluating queries. These lists can either allow or deny access to specific domains. For example, you might create a domain list that blocks access to known malicious domains or another that allows only trusted domains. AWS provides managed domain lists that are regularly updated with threat intelligence, and administrators can combine them with custom lists for stronger protection. Domain lists are central to building rules because each rule requires at least one domain list to function.
4. Domain Redirection Settings
DNS queries often involve redirection chains, such as CNAME or DNAME records, where one domain points to another. The domain redirection setting in DNS Firewall lets you decide whether to inspect the entire chain of redirections or only the first domain in the chain. By default, DNS Firewall inspects the entire chain, which provides deeper security but requires that you also include redirected domains in your domain list. If you prefer to trust the redirection after the first domain, you can configure DNS Firewall to inspect only the initial domain. This flexibility ensures a balance between performance and security.
5. Query Type Settings
The query type setting enables administrators to filter DNS queries based on their type. For example, you might want to block all query types for a particular domain but allow only MX queries if the domain is needed for email delivery. If you don’t specify a query type, the rule applies to all types of queries by default. This setting is useful in scenarios where only specific DNS records are necessary for functionality, while others could be abused or unnecessary.
6. DNS Firewall Advanced Protection
The advanced protection feature in DNS Firewall goes beyond simple domain allow/deny lists. It uses AWS-managed threat intelligence to detect malicious behavior. This includes protection against Domain Generation Algorithms (DGAs), which are used by attackers to create large numbers of dynamic domains for malware communication, and DNS tunneling, which is a technique for exfiltrating data using DNS queries. With advanced protection, administrators can choose whether to block these suspicious queries entirely or just generate alerts. Since AWS continuously updates the protection algorithms, your VPCs remain guarded against evolving threats without requiring manual updates.
7. Confidence Threshold (Advanced Protection Only)
When configuring advanced protection, you must set a confidence threshold that defines the strictness of detection. There are three levels: High, Medium, and Low. A high confidence threshold ensures only the most reliable and verified threats are blocked, minimizing false positives. Medium provides a balance between detection and accuracy, suitable for most use cases. Low maximizes threat detection but can also increase the number of false positives. This flexibility allows organizations to adjust protection based on their tolerance for risk and operational needs.
8. Association Between Rule Groups and VPCs
To activate DNS Firewall protection, administrators must associate rule groups with VPCs. This association links the filtering logic to the network where DNS queries originate. If multiple rule groups are associated with a VPC, they are applied sequentially based on their assigned priority. This layered approach allows organizations to apply different sets of rules for different use cases—for example, blocking known malicious domains first, then applying additional allowlists or custom rules afterward.
9. Resolver DNS Firewall Configuration for a VPC
Once a rule group is associated with a VPC, you must configure how Route 53 Resolver should handle DNS queries in relation to the firewall. By default, DNS Firewall uses a fail-closed mechanism. This means that if the firewall cannot provide a filtering decision for a DNS query, the query is automatically blocked. This behavior ensures security is prioritized over availability, preventing unfiltered queries from bypassing the firewall.
10. Monitoring DNS Firewall Actions
Monitoring is an essential part of DNS security. DNS Firewall integrates with AWS services to provide visibility into its actions. Amazon CloudWatch collects metrics about the number of queries that are allowed, blocked, or alerted on by rule groups. This enables near real-time monitoring and trend analysis. Additionally, Amazon EventBridge allows you to build event-driven workflows that respond to DNS Firewall events, such as automatically notifying security teams when suspicious queries are detected. These integrations ensure that administrators not only protect DNS traffic but also gain actionable insights for improving security posture.
Benefits of Using Dns Firewall
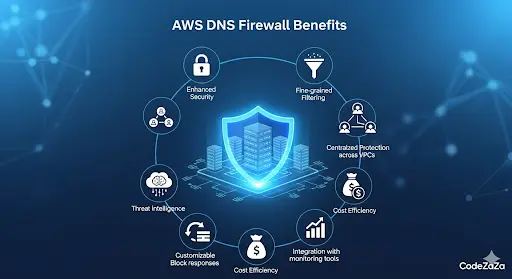
1. Enhanced Security Against DNS Threats
One of the biggest benefits of using AWS DNS Firewall is its ability to protect your VPC from DNS-based threats such as malware domains, phishing attacks, DNS tunneling, and Domain Generation Algorithms (DGAs). By filtering DNS queries, it ensures that malicious traffic is stopped before it reaches your applications, reducing the risk of data breaches or command-and-control attacks.
2. Fine-Grained DNS Query Filtering
DNS Firewall allows you to create customizable rules to block, allow, or alert on specific domain queries. You can filter based on domain lists, query types (such as MX or A records), or advanced threat intelligence. This level of control means you can tailor security policies to fit your business requirements, ensuring flexibility and precision in protection.
3. Centralized Protection Across Multiple VPCs
With rule groups, you can apply a consistent set of filtering policies across multiple VPCs in your AWS environment. This provides centralized management of DNS security policies, ensuring compliance and uniform security standards across your entire cloud infrastructure.
4. Integration with AWS Managed Threat Intelligence
AWS DNS Firewall comes with AWS-managed domain lists and advanced protection features. These include continuously updated intelligence against known threats such as DGAs and tunneling attempts. Since AWS maintains and updates these protections, your security posture is always aligned with the latest threat landscape, reducing the need for manual updates.
5. Improved Cost and Operational Efficiency
DNS Firewall is a fully managed service, meaning AWS handles the infrastructure and scaling. You don’t need to deploy and maintain third-party DNS security appliances. This reduces operational overhead and costs while still ensuring enterprise-grade DNS filtering at scale.
6. Customizable Block Responses
Instead of simply dropping queries, DNS Firewall lets you configure custom responses for blocked domains. For example, you can redirect users to a safe landing page or provide a specific DNS error message. This improves user experience while still maintaining strict security.
7. Integration with AWS Monitoring and Automation Tools
DNS Firewall integrates seamlessly with Amazon CloudWatch and Amazon EventBridge, giving you real-time visibility into DNS query activity. You can monitor allowed, blocked, or alerted queries, set up alarms for unusual activity, and even trigger automated workflows for incident response.
Conclusion
Route 53 Resolver DNS Firewall offers a comprehensive DNS security framework within AWS. By using rule groups, domain lists, query type filters, and advanced threat detection, organizations can take control over DNS traffic in their VPCs. The firewall helps mitigate DNS tunneling, malware communication via DGAs, and access to malicious domains. Its integration with CloudWatch and EventBridge ensures complete visibility and automation. With fine-grained settings like domain redirection control and confidence thresholds, DNS Firewall provides both flexibility and strong protection, making it an essential part of securing workloads in the cloud.


