Kubernetes Service
The definition of Kubernetes services refers to a” Service which is a method for exposing a network application that is running as one or more Pods in your cluster.” Service is a static IP address or a permanent IP address that can be attached to the Pod. We need Service because the life cycles of Service and the Pod are not connected, so even if the Pod dies, the Service and its IP address will stay so we don’t have to change that endpoint every time the Pod dies.
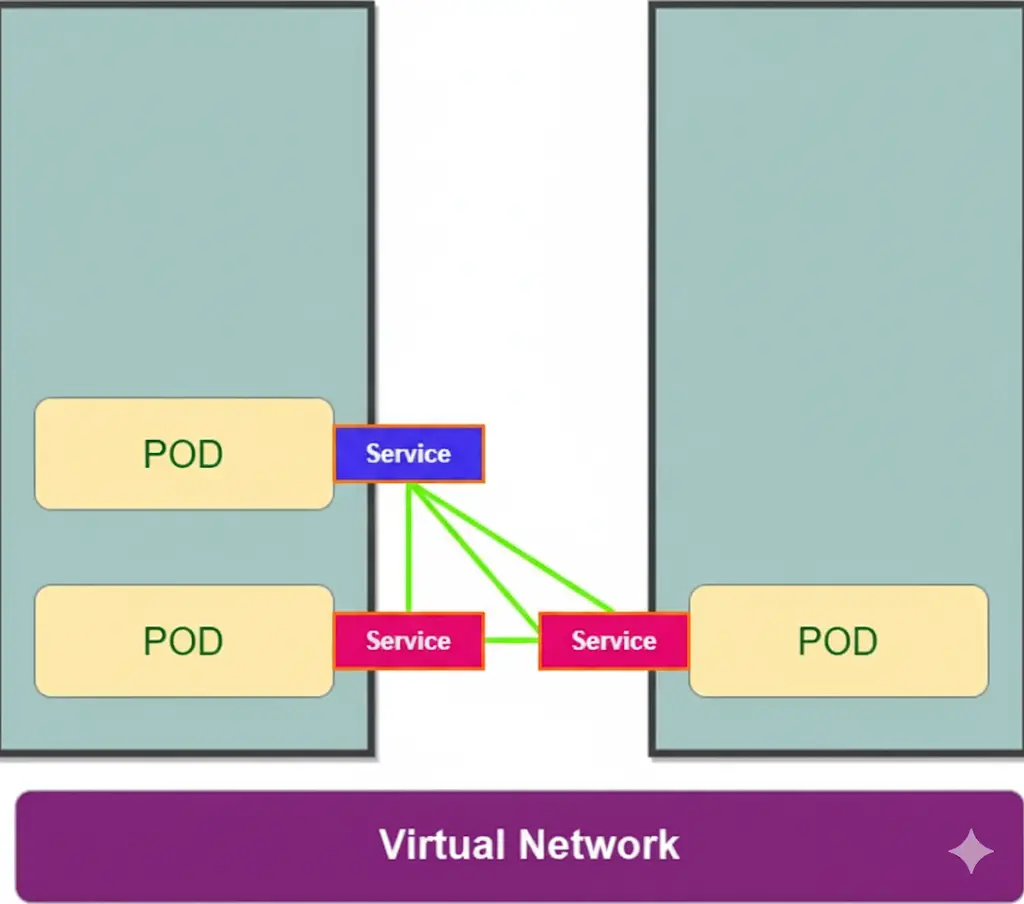
Therefore, what Service does is it provides stable IP address to the Pods. A Kubernetes Service also provides load balancing because when you have pod replicas, For example, three replicas of a microservice application. The Service will basically get request targeted to the application and forward it to one of those pods. Because of this now clients can call a single stable IP Address instead of calling each pod individually, so services are a good abstraction for loose coupling and for communication within the cluster and outside it as well.
Why Services Are Needed in Kubernetes
Kubernetes clusters use a distributed architecture, so you need Services to manage communication. Applications run as Pods, and you can have thousands of replicas spread across hundreds of compute Nodes. When a user interacts with your app, Kubernetes must route the request to any available replica, regardless of its location.
Services manage this routing. All network traffic first reaches a Service. The Service then forwards it to one of the available Pods. Other applications can contact the Service using its IP address or DNS name. This approach ensures reliable communication with your Pods.
Kubernetes provides automatic DNS for Services through its service discovery system. Each Service gets a DNS A or AAAA record in the format <service-name>.<namespace-name>.svc.cluster-domain>. For instance, a Service named demo in the default namespace appears as demo.default.svc.cluster.local within the cluster. This setup allows applications to connect reliably without looking up Pod IPs manually.
Kubernetes Service types
All Kubernetes Services ultimately forward network traffic to the Pods they represent. Kubernetes provides five main types of services, each type controls how traffic is routed to pods, and the choice depends on visibility and routing requirements:
- ClusterIP – Default, internal-only access within the cluster
- NodePort – Exposes service on each node’s IP at a static port
- LoadBalancer – Creates external load balancer for public access (cloud only)
- ExternalName – Maps service to an external DNS name, no proxying
- Headless – No cluster IP, exposes individual pod IPs
Here’s how the five currently available options compare:
1. ClusterIP Service
ClusterIP is the most common Service as well as it is the Default type of Service, meaning when you create a Service and not specify a type it will automatically take ClusterIP as a type.
Let’s understand this with the help of an example. Imagine we have a microservice application deployed in the Cluster. We have a Pod with microservice container running inside it and beside that microservice container we have a side-car container that collects the logs of the microservice and then sends that to some destination database.
apiVersion: apps/v1
kind: Deployment
metadata:
name: microservice-one
# ...
spec:
replicas: 3
# ...
template:
metadata:
labels:
app: microservice-one
spec:
containers:
- name: ms-one
image: my-repo/ms-one
ports:
- containerPort: 3000
- name: log-collector
image: my-repo/log-c
ports:
- containerPort: 9000
Here, our microservice container (ms-one) is running at Port 3000 and the logging container is running on Port 9000. This means that those two ports will be now open and accessible inside the Pod. The Pod will also get an IP address from a range that is assigned to a node.
2. NodePort
NodePort is a Service that is accessible on a static Port on each Worker Node in the cluster. The NodePort Service makes the external traffic accessible on static or fixed port on each worker Node which is different from the ClusterIP Service which was only accessible within the Cluster (no external traffic can directly address the ClusterIP Service). With NodePort instead of Ingress, the browser request will come directly to the worker node at the Port that the service specification defines and the Port that NodePort service type exposes is defined in the NodePort attribute. The NodePort value has a predefined range between 30,000 and 32,767.
apiVersion: v1
kind: Service
metadata:
name: ms-service-nodeport
spec:
type: NodePort
selector:
app: microservice-one
ports:
- protocols: TCP
port: 3200
targetPort: 3000
nodePort: 30008
The NodePort Service is accessible for the external traffic like browser request. NodePort Service exposure is not very efficient and not secure because we are opening the Ports to directly talk to the Services on each Worker Node so the external clients basically have access to the worker nodes directly, so if we gave all the services this NodePort Service type then we would have a bunch of Ports open on the worker nodes Clients from outside can directly talk to.pe you should normally use when you need an app to be accessible outside Kubernetes.
3. Load Balancer
Load Balancer Service type allows the Service to become accessible externally through a Cloud Provider’s Load Balancer functionality. LoadBalancer Service is an extension of NodePort Service. To understand LoadBalancer Service type, you must know about Load Balancing. Load Balancing is the process of dividing a set of tasks over a set of resources in order to make the process fast and efficient. All the Cloud Providers like Google Cloud Platform, AWS, Azure, etc. have their own native Load Balancer implementation and that is created and used whenever we create a LoadBalancer Service type.
Whenever we create a LoadBalancer Service, NodePort and ClusterIP Services are created automatically by Kubernetes to which the external Load Balancer of the cloud platform will route the traffic to. Here is an example of how to define load balancer service configuration:
apiVersion: v1
kind: Service
metadata:
name: ms-service-loadbalancer
spec:
type: LoadBalancer
selector:
app: microservice-one
ports:
- protocols: TCP
port: 3200
targetPort: 3000
nodePort: 30010
Here the nodePort which is the port that opens on the Worker Node is not directly accessible externally but only through the Load Balancer. So the entry point becomes a Load Balancer first and it can then direct the traffic to nodePort on the Worker Node and the ClusterIP. Hence we can say that the LoadBalancer Service type is an extension of the NodePort type which itself is an extension of the ClusterIP Service type.
4. ExternalName Services
ExternalName Services allow you to conveniently access external resources from within your Kubernetes cluster. Unlike the other Service types, they don’t proxy traffic to your Pods.
When you create an ExternalName Service, you have to set the spec.externalName manifest field to the external address you want to route to (such as example.com). Kubernetes then adds a CNAME DNS record to your cluster that resolves the Service’s internal address (such as my-external-service.app-namespace.svc.cluster.local) to the external address (example.com). This allows you to easily change the external address in the future, without having to reconfigure the workloads that refer to it.
5. Headless Services
Headless services are a special type of Service that don’t provide load balancing or a cluster IP address. They’re “headless” because Kubernetes doesn’t automatically proxy any traffic through them. This allows you to use DNS lookups to discover the individual IP addresses of any Pods selected by the Service.
A headless service is useful when you want to interface with other service discovery systems without kube-proxy interfering. You can create one by specifically setting a Service’s spec.clusterIP field to the None value.
Which Service type should I use?
The correct Kubernetes Service type for a particular workload primarily depends on whether you’ll need external access. If you will interact with a Service from outside Kubernetes, then LoadBalancers should be preferred. A NodePort Service can be useful instead if you can accept its tradeoffs, a load balancer integration is unavailable, or you plan to implement your own load balancing solution.
For workloads that will only be accessed within your cluster—typically including database connections, caches, and other internal system components—ClusterIPs should be used to prevent inadvertently exposing the Service. Developers and operators can still connect to these Services from their workstations to debug problems and manually interact with workloads using the port-forwarding features available in Kubectl.
Here’s a quick tabular summary of how each Service type compares.
| Characteristic | ClusterIP | NodePort | LoadBalancer | ExternalName | Headless |
| Accessibility | Internal | External | External | Internal | Internal |
| Use case | Expose Pods to other Pods in your cluster | Expose Pods on a specific Port of each Node | Expose Pods using a cloud load balancer resource | Configure a cluster DNS CNAME record that resolves to a specified address | Interface with external service discovery systems |
| Suitable for | Internal communications between workloads | Accessing workloads outside the cluster, for one-off or development use | Serving publicly accessible web apps and APIs in production | Decoupling your workloads from direct dependencies on external service URLs | Advanced custom networking that avoids automatic Kubernetes proxying |
| Client connection type | Stable cluster-internal IP address or DNS name | Port on Node IP address | IP address of external load balancer | Stable cluster-internal IP address or DNS name | Stable-cluster internal IP address or DNS name that also enables DNS resolution of the Pod IPs behind the Service |
| External dependencies | None | Free port on each Node | A Load Balancer component (typically billable by your cloud provider) | None | None |
Best Practices for Using Kubernetes Services
- Use Labels and Selectors Consistently:
Always label your Pods clearly and design selectors in Services carefully. This ensures Services target the correct Pods, avoids accidental misrouting, and simplifies scaling or updates. - Choose the Right Service Type:
Pick the Service type based on your use case:- Use ClusterIP for internal communication within the cluster.
- Use NodePort for quick external access during development.
- Use LoadBalancer for production-ready external traffic with cloud integration.
- Use ExternalName to connect to external services via DNS.
- Keep Service Endpoints Minimal:
Only expose the Pods that truly need to be accessed through a Service. Avoid exposing all Pods unnecessarily, which can improve security and reduce potential misconfigurations. - Secure Services Using Network Policies:
Combine Services with Kubernetes Network Policies to control traffic flow. This ensures that only authorized Pods or clients can access the Service, improving cluster security. - Use Headless Services When Needed:
For applications that require direct Pod-to-Pod communication (e.g., stateful applications like databases), use headless Services (clusterIP: None) to expose individual Pod endpoints without load balancing. - Monitor and Label Traffic:
Apply meaningful labels to Services and monitor traffic using tools like Prometheus or Grafana. This helps track usage, troubleshoot issues, and maintain proper observability. - Avoid Hardcoding Service Names:
Always refer to Services by their DNS names within the cluster (e.g.,my-service.default.svc.cluster.local) instead of hardcoding IPs. This ensures Pods can communicate reliably even if the endpoints change. - Version and Environment Segregation:
Use labels likeapp=v1orenv=stagingto separate Service endpoints by version or environment. This practice avoids conflicts and supports smooth rolling updates or A/B testing.
Conclusion
In this article we have discussed the most important types of Service in Kubernetes. Service is basically a static IP address or a permanent IP address that can be attached to the Pod. The reason why we need Service is that the life cycles of Service and the Pod are not connected so even if the Pod dies, the Service and its IP address will stay so we don’t have to change that endpoints every time the Pod dies. In this article we discussed for types of Services – ClusterIP, NortPort, LoadBalancer and Headless Service.
We hope that this article helped you improve your understanding about Services in Kubernetes. Make sure to go through the entire article for in-depth understanding Services.


