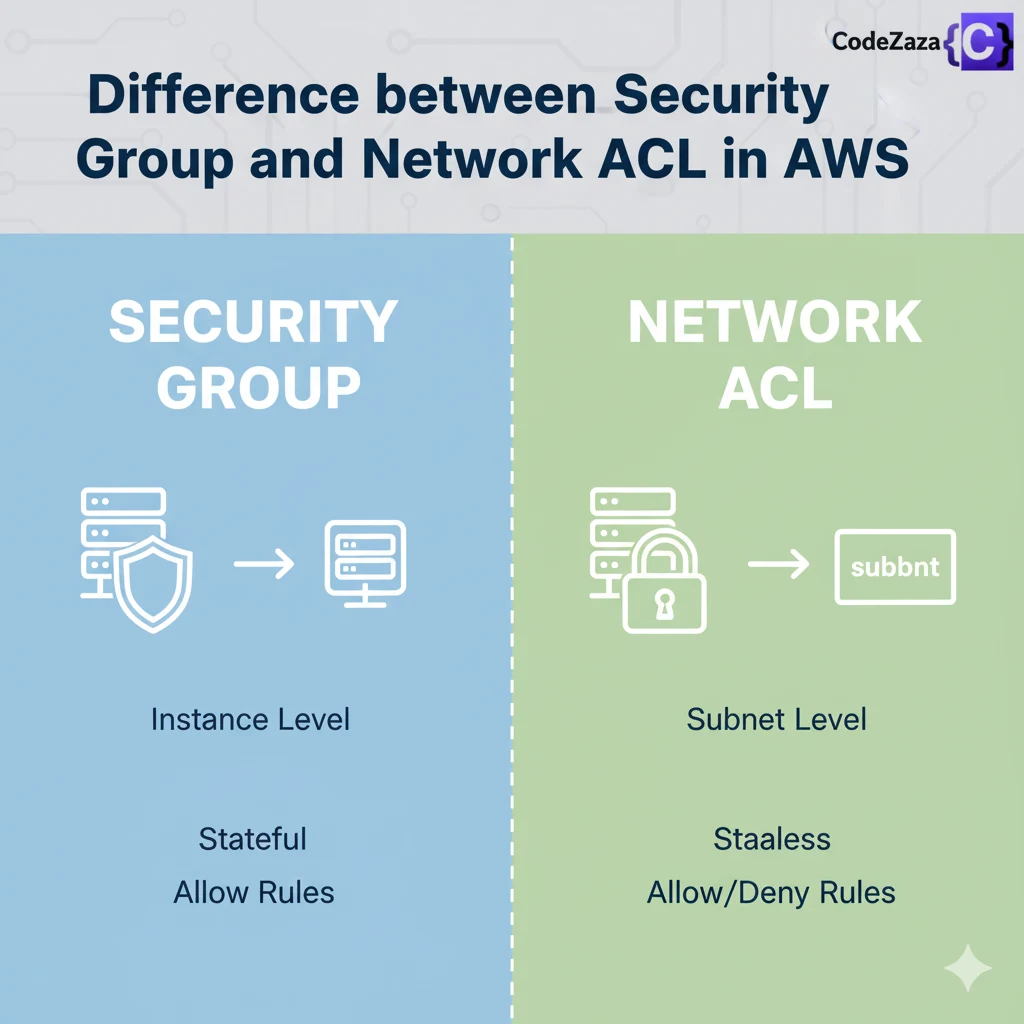
AWS network security is a critical foundation when deploying resources in an Amazon Virtual Private Cloud (VPC). Two primary components help you control access within a VPC: Security Groups and Network Access Control Lists (NACLs).
While both regulate inbound and outbound traffic to your AWS resources, they operate differently. Understanding the difference between Security Group and Network ACL in AWS is essential for designing secure and efficient network architectures. In this article, we will explore these differences, their key features, and when to use each for optimal VPC security.
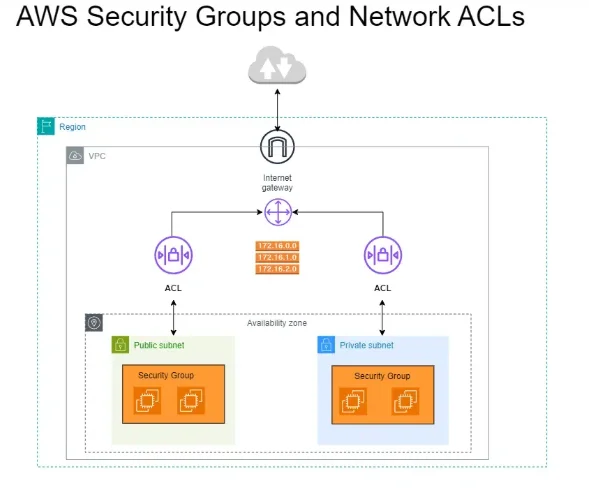
What is AWS Security Group?
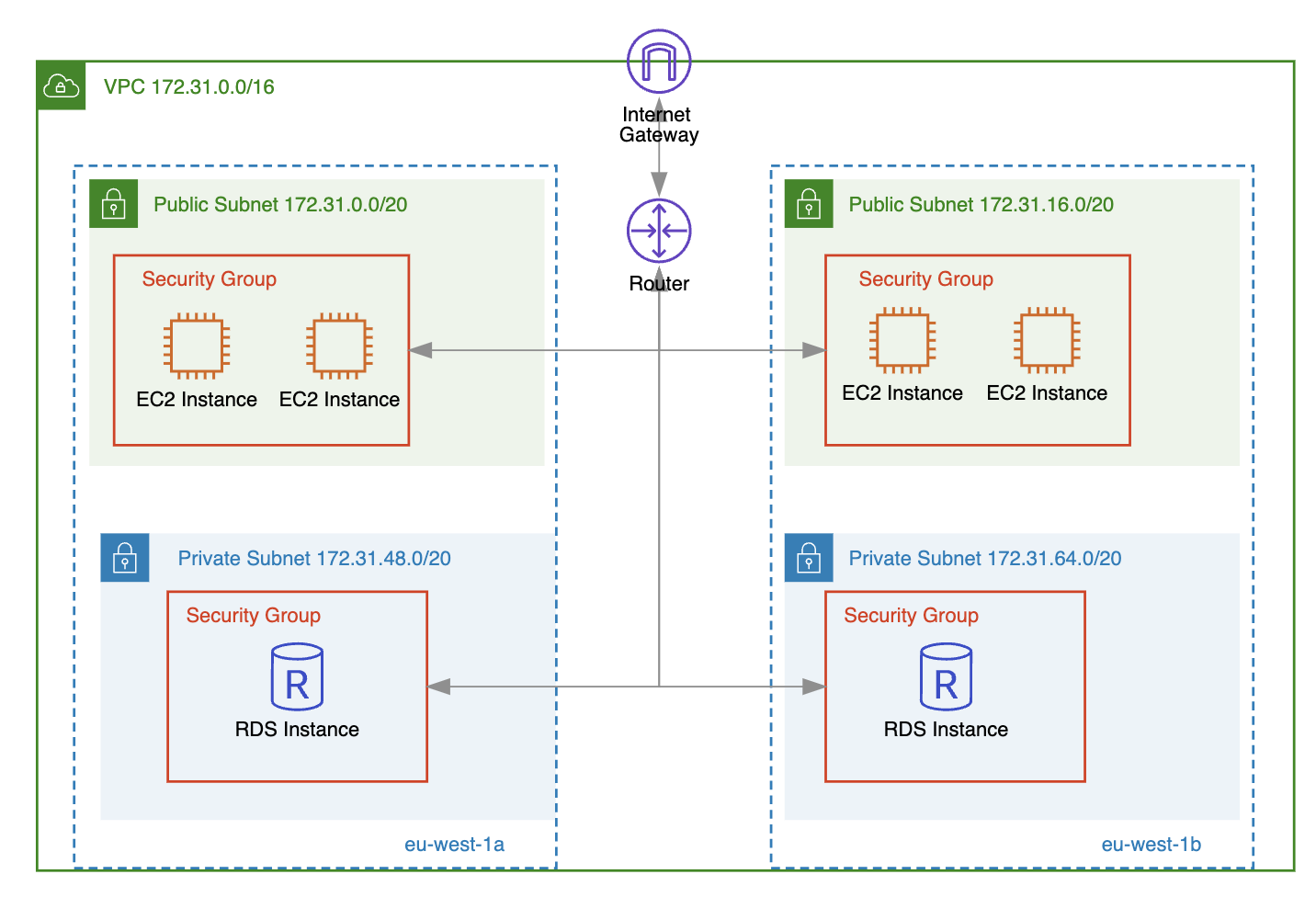
A security group acts as a virtual firewall that controls the traffic allowed to reach and leave AWS resources (like EC2 instances, load balancers, RDS database instances, VPC endpoint interfaces, Redis instances, etc.) within your VPC.
When creating new inbound and outbound rules, you need to specify the following:
- Protocol: The protocol to allow (e.g., TCP, UDP, ICMP).
- Port range: The range of ports to allow (e.g., 22, 3500-3510).
- Source/destination: The source or destination for the allowed traffic (e.g., IP address, another security group).
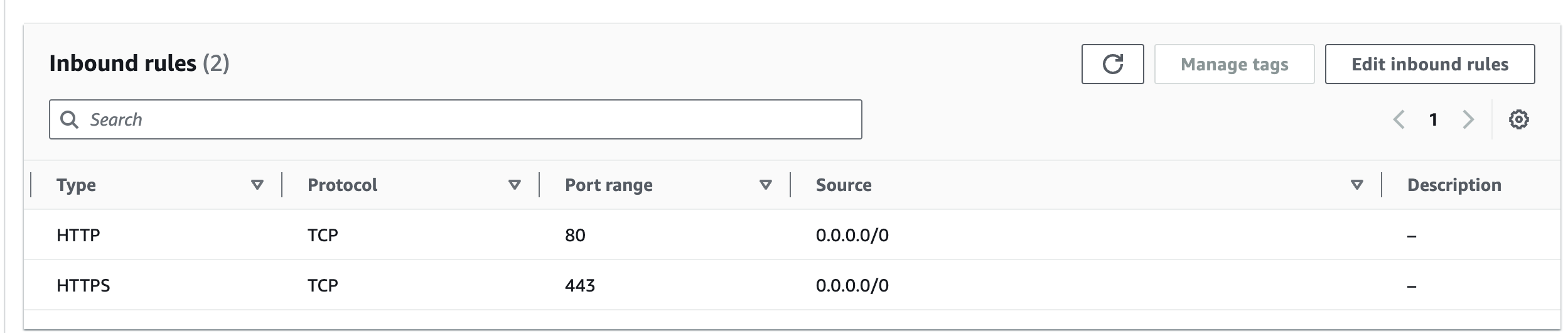
In the example below, we have added two rules to a security group that allow TCP traffic on ports 443 and 80 from any IP address. Since these ports are used for HTTP/HTTPS traffic, this means that if you run your own web servers on public EC2 instances with this security group assigned, anyone could now access your website.
What is AWS Network Access Control List?
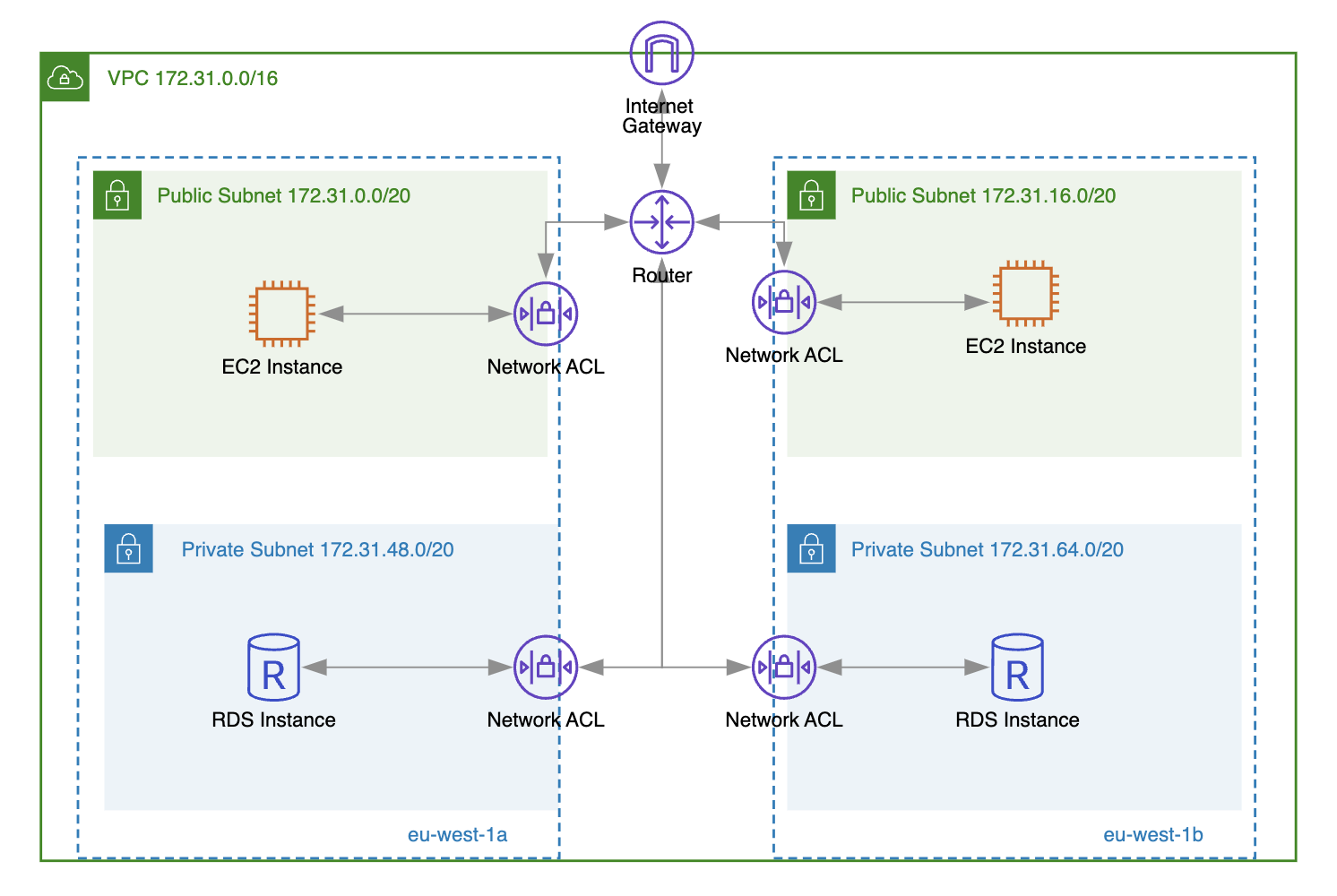
Network access control list (NACL) acts as a virtual firewall to allow or deny inbound or outbound traffic at subnet level. Similar to security groups, you can create new inbound and outbound rules for network ACL by providing:
- Rule number: The priority of the rule (lowest number has highest priority) that will be effective in case there are other rules.
- Protocol: The protocol to allow (e.g., TCP, UDP, ICMP).
- Port range: The range of ports to allow (e.g., 443, 4000-4010).
- Source/destination: The source or destination for the allowed traffic.
- Allow/deny flag: Whether to allow or deny the traffic
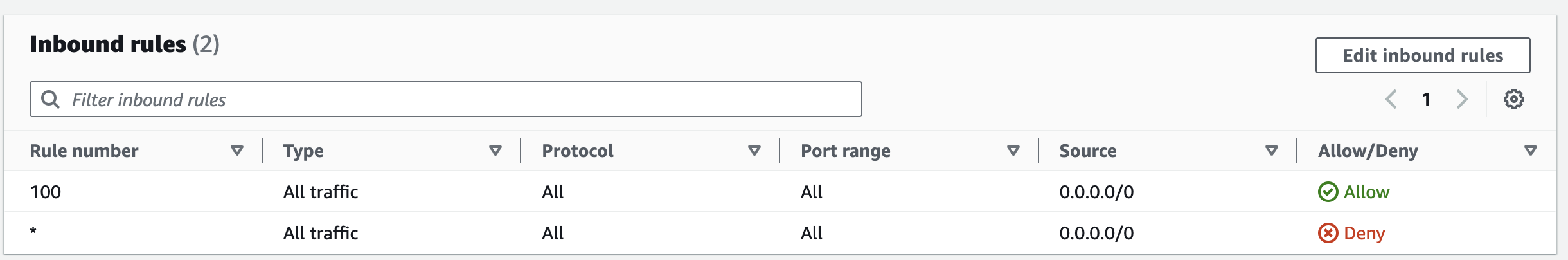
In the example below, you can see the default NACL inbound rules (by default associated to all the subnets in VPC). The first rule allows all inbound traffic from any source, while the last rule denies all traffic and would be effective if no other allow rules are specified.
What is the difference between Security Group and Network ACL ?
The following are the difference between Security Groups and Network ACLs:
| Security Group | Network Access Control List |
|---|---|
| In security group, we operate at instance level. | In network ACL, we operate sub net level. |
| It support only allow rules. | It support allow rules and deny rules. |
| It is stateful, when we create an inbound or an outbound rule. | It is stateless, it return traffic must be allowed explicitly. |
| We cannot block specific IP address using SGs. | We can block specific IP Address using NACL. |
| All rules are evaluated before deciding to permit trffic. | Rules are processed in number order when deciding whether allow traffic. |
| It start with instance launch configuration. | In which we assigned to subnet for all instance. |
| It applies when someone specifies security group when launching the instance and it associates with security group. | They do not depend on user it automatically apply all instances with subnet. |
What is the difference between Network ACL and Route Table?
The following are the differences between Network ACL and Route Table:
| Aspect | Network ACL | Route Table |
|---|---|---|
| Location | It operates the subnet level within a VPC | It operates at the VPC level affecting all subnets |
| Function | It controls the traffic that is entering and leaving in subnets. | It directs the traffic between subnets and internet. |
| Rules Application | It processes the rules in sequentially based on the priority. | It routes the traffic based on the destination IP addresses. |
| Default Action | Its default action is to ney all the traffic | It default action is to route the traffic to the target |
| Use Cases | It used for implementing the network level security policies | It used for defining how traffic is routed within the VPC. |
How to Control Traffic to Subnets Using Network ACLs: A Step-by-Step Guide
Controlling traffic to subnets in AWS using Network ACLs (NACLs) can help secure your VPC. Follow these steps:
Step 1: Create a Network ACL
Start by creating a Network ACL in your VPC. You can do this through the AWS Management Console or by using AWS CLI commands.
Step 2: Associate the Network ACL with Subnets
After creating the NACL, associate it with the subnets where you want to manage traffic. Note that a single NACL can protect multiple subnets, but each subnet can only have one NACL at a time.
Step 3: Define Inbound and Outbound Rules
Next, configure inbound and outbound rules to allow or deny specific types of traffic. AWS evaluates rules in numerical order, starting with the lowest number.
Step 4: Prioritize Rules
Arrange your rules according to priority. Place the most specific rules at the top and the more general ones at the bottom to ensure the correct rule evaluation.
Step 5: Configure Rule Actions
For each rule, define whether the traffic should be allowed or denied based on your security requirements. For example, allow HTTP and HTTPS traffic while denying access from certain IP addresses or protocols.
Finally, apply the changes. The updated rules take effect immediately and start controlling traffic to the associated subnets.
Troubleshooting of Security Groups And Network ACLs
The following are the some of the troubleshootings of Security Groups and Network ACLs:
- Review Rules Configuration: Try on reviewing the rules that are configured in both the security groups and network ACLs. Check for any misconfigurations or conflicting rules that causing the issues.
- Check Logging and Monitoring: Look on utilizing of AWS CloudWatch Logs and VPC Flow Logs to monitor and analyze the network traffic. It looks for any denied or dropped connections that could indicates the issues with the security groups or Network ACLs.
- Check Associated Resources: Confirmation of the security groups and network ACLs are correctly associated with the intended resources such as EC2 instances or subnets for ensuring the changes that made for security groups or NACLs that are properly appling to associated resources.
Conclusion
Both Security Groups (SGs) and Network ACLs (NACLs) help control traffic in your AWS VPC, but they serve different purposes and operate differently:
- Security Groups act as virtual firewalls at the instance level, controlling inbound and outbound traffic for EC2 instances. They are stateful, meaning if an incoming request is allowed, the response is automatically allowed.
- Network ACLs operate at the subnet level, controlling traffic entering or leaving the subnet. They are stateless, so inbound and outbound rules must be explicitly defined for traffic to flow in both directions.
In essence, use Security Groups for fine-grained instance-level control and NACLs for broader subnet-level traffic filtering. Combining both gives a layered security approach in your AWS environment.