As cloud environments grow more complex, securing traffic in and out of your Virtual Private Cloud (VPC) is critical. AWS Network Firewall is a managed firewall service that allows organizations to protect their VPCs from network threats while providing flexible control over inbound and outbound traffic.
Whether you are an AWS beginner or an experienced cloud engineer, understanding ANetwork Firewall is essential for building secure cloud architectures.
What is AWS Network Firewall?
Think of AWS Network Firewall as a digital guard that protects your cloud environment from cyber-attacks, unwanted traffic, and bad actors. AWS provides this fully managed security service to protect your Amazon Virtual Private Cloud (VPC). It inspects and filters traffic flowing in and out of your cloud network to keep it safe.
AWS Network Firewall offers several powerful features:
Intrusion Prevention: Identifies and stops attacks such as malware or DDoS attempts.res, including:
Deep Packet Inspection: Scans network data to detect harmful traffic.
Customizable Security Rules: Lets you define which traffic to allow or block.
- Deep Packet Inspection: Scanning the data moving across your network to catch harmful traffic.
- Customizable Security Rules: You can set up your own rules to control which traffic is allowed or blocked.
- Intrusion Prevention: Identifies and stops potential attacks like malware and DDoS attacks.
Why Network Firewall?
A Network Firewall is important for protecting your cloud infrastructure and ensuring the safety of your data. Here’s why it’s needed:
1. Traffic Control
It helps you manage the flow of data in and out of your cloud network, blocking bad traffic and allowing safe, authorized traffic to pass through.
2. Threat Protection
It defends your network against cyber-attacks, such as DDoS attacks (where attackers try to overwhelm your network) and malware, ensuring your data stays secure.
3. Network Segmentation
AWS Network Firewall helps break your network into smaller parts, which means you can apply stronger security to the most important areas of your infrastructure.
4. Compliance
Many industries have strict security regulations (like healthcare or finance). AWS Network Firewall helps meet these standards by enforcing security rules and keeping track of everything.
5. Scalability
As your business grows, so does your need for security. AWS Network Firewall scales automatically to match your network size and keeps your system protected as it grows.
6. Visibility
It gives you insight into your network traffic, allowing you to spot unusual activity or security threats before they cause harm.
How Does AWS Network Firewall Work?
Setting up AWS Network Firewall is straightforward, and here’s how it works:
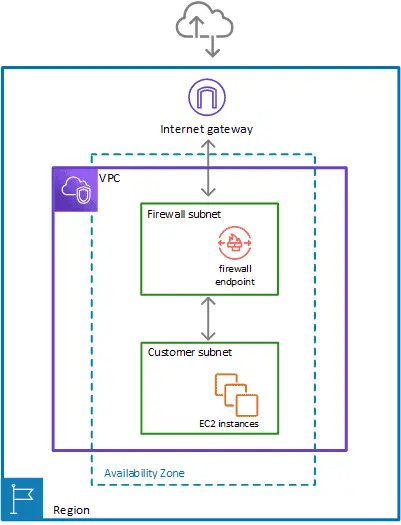
- Firewall Endpoint:
AWS Network Firewall uses something called a firewall endpoint. This is where all the traffic from your network gets sent for inspection. Think of it as the entry gate where data is checked before entering or leaving your network. - Traffic Inspection:
Once the traffic reaches the firewall endpoint, it gets examined to see if it’s safe. If it passes all the checks, it’s allowed to continue. If it’s malicious or doesn’t meet security standards, it gets blocked. - Routing Traffic:
You need to tell AWS how to route your traffic to the firewall. You can do this using VPC route tables, which are settings that define how data moves around in your network. For example, you can set it up so that traffic going from your applications to the internet is inspected by the firewall. - No Changes to Traffic:
One cool thing about AWS Network Firewall is that it doesn’t change the data. It keeps the source and destination IPs intact, meaning your traffic looks exactly the same after passing through the firewall.
A Simple Lab Setup Guide
Step 1: Setting up the environment.
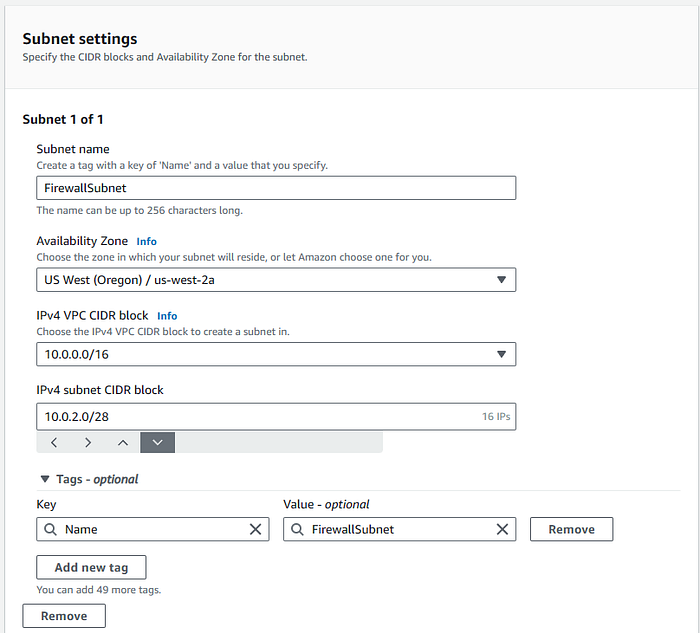
Create a dedicated subnet for the Network Firewall.
- Go to VPC >> Subnets >> Create a Subnet
Note: A Network Firewall needs a dedicated subnet with a /28 or larger IP space.
Network Firewall — Rule Groups
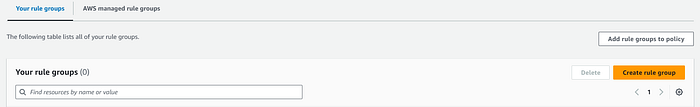
Once you set up the subnet, the next step is to create Network Firewall Rule Groups.
Think of a rule group as a collection of rules that control how traffic flows through AWS Network Firewall. These rules determine whether traffic is allowed or blocked based on specific criteria. Moreover, rule groups play a crucial role in defining and enforcing security policies for your firewall.
- On you VPC Dashboard go to: Network Firewall >> Network Firewall rule groups.

In AWS Network Firewall, there are two main types of rule groups:
- Stateful: These are like smart rules that understand the context of network traffic. They can allow or block traffic based on things like source, destination, and more. Think of them as traffic cops that can make decisions based on what they see.
- Stateless: These are more like basic traffic filters. They follow simple rules to either allow or block traffic, without understanding the context. It’s like a list of specific traffic rules that are applied without considering the bigger picture.
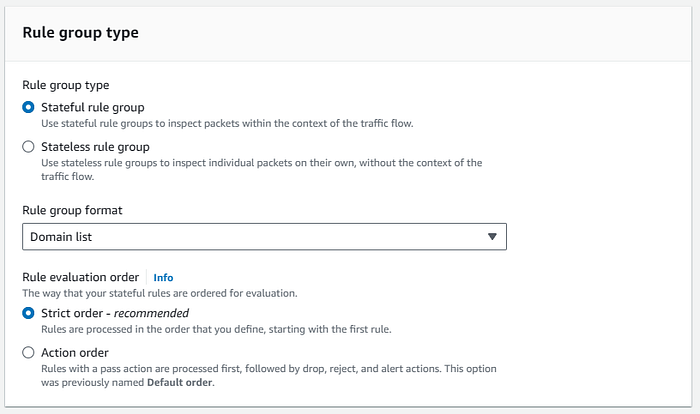
We will create three type of rule groups:
- Stateful group for Domain List
- Stateful group standard
- Stateless
Stateful group for Domain List
Domain List Rule Group is designed to filter and control network traffic based on domain names, which are like web addresses. You can create a list of domain names that you want to allow or block. This rule group is especially useful for managing access to specific websites or online services.

Note: Capacity is the number of rules you expect to have in this rule group during its lifetime. You can’t change capacity after rule group creation, so leave room to grow.
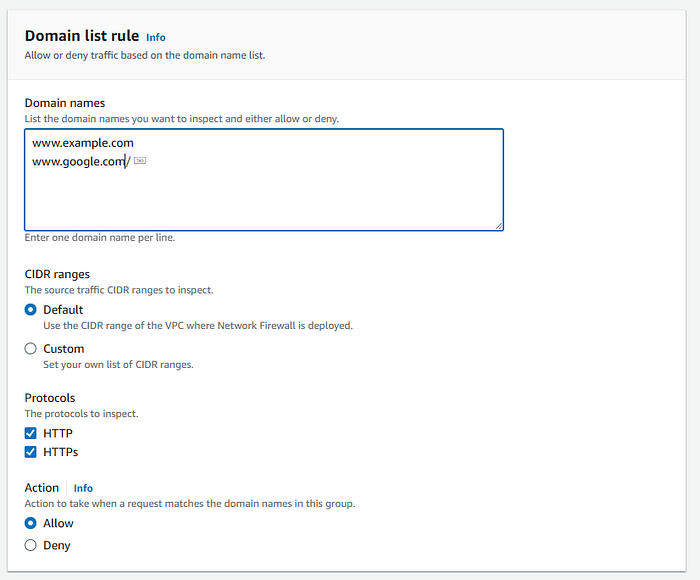
You can list all the domains that you would like to inspect to either allow or deny.
We will use the following examples:
For now, we will keep the Action to “Allow”.
Stateful groups Standard
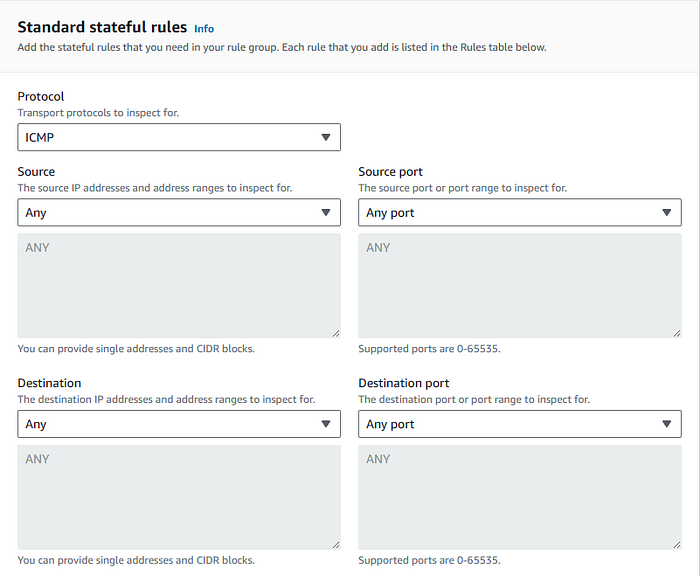
This is a more general-purpose rule group that can be customized to match your specific network security needs. It allows us to define rules based on unique requirements, making it versatile for various use cases.
For example, we can specify the values for Layer 3 and Layer 4.
For our lab, we will create an ICMP group rule, and as before, we keep the action as “Pass”.
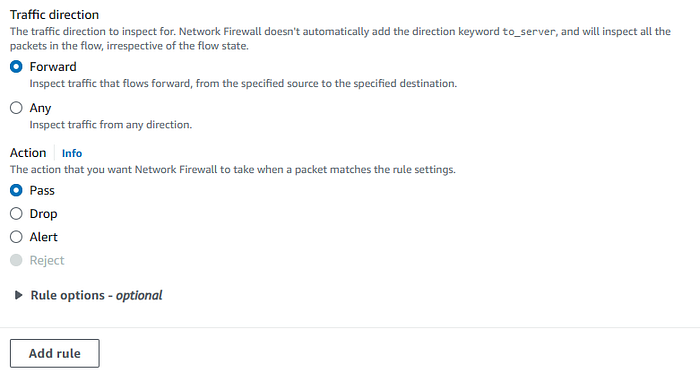
Stateless group
A stateless rule group in AWS Network Firewall is like a basic set of traffic rules. It decides what traffic can come in and go out of your network, but it doesn’t remember previous actions or understand the bigger picture of the traffic flow. It’s a bit like a gatekeeper checking each person’s ID at the door without knowing anything about them except what’s on the ID. Simple and effective for straightforward security needs.
For our lab, we will create a simple Stateless rule group for all the traffic in and out of our VPC.
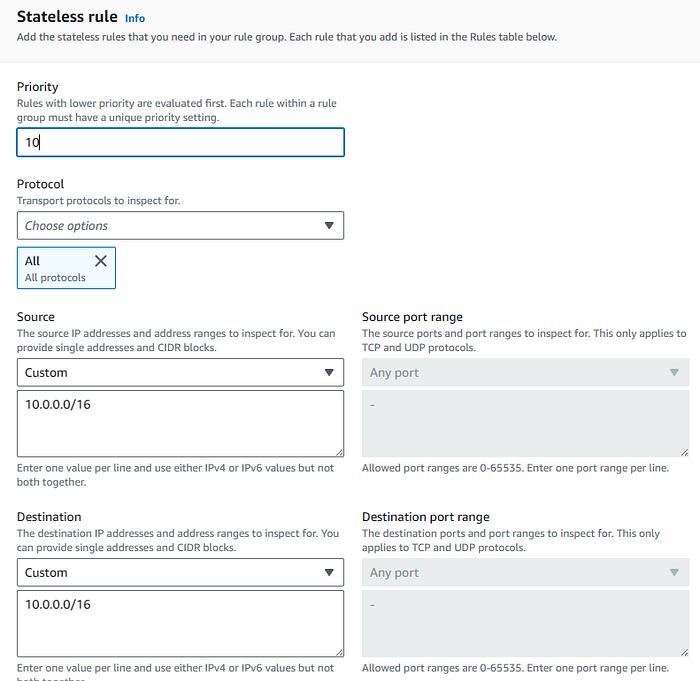
After all the Rule groups are created, we should have a list simimar to:
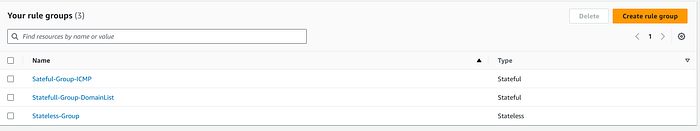
Step 2: Creating a Network Firewall Policy
An AWS Network Firewall policy defines the monitoring and protection behavior for a firewall. The details of the behavior are defined in the rule groups that you add to your policy, and in some policy default settings. To use a firewall policy, you associate it with one or more firewalls.
- On your VPC Dashboard go to: Network Firewall >> Firewall Policies and “Click” on create.

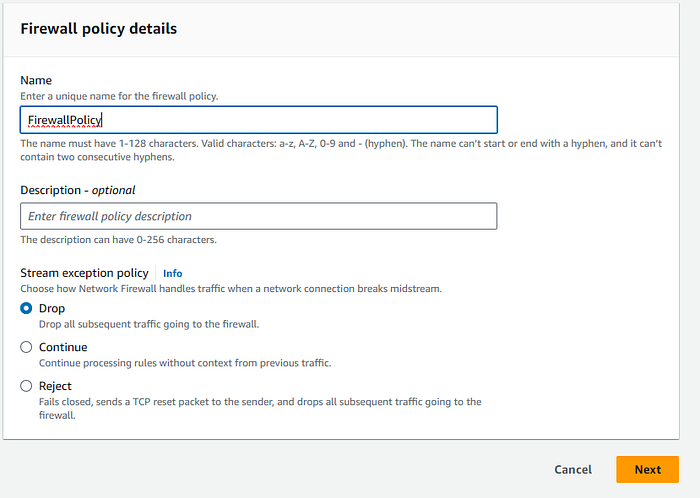
Select the Stateless rule group created previusly.
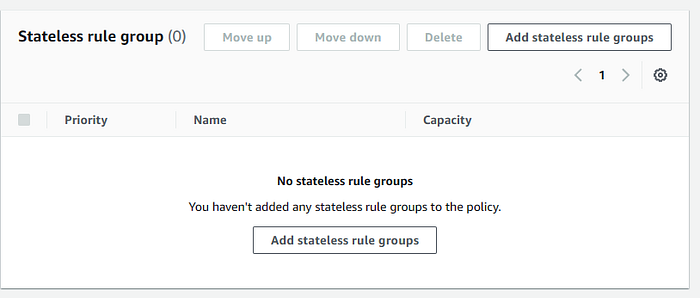
Select both stateful rule group created previusly.
Click on “Create Firewall Policy”
Step 3: Creating a Network Firewall
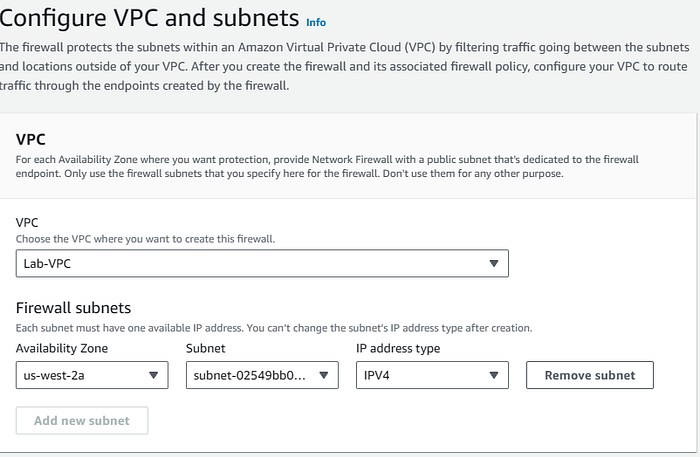
An AWS Network Firewall connects a firewall policy, which defines network traffic monitoring and filtering behavior, to the VPC that you want to protect.
The firewall configuration includes specifications for the Availability Zones and subnets where the firewall endpoints are placed. It also defines high-level settings like the firewall logging configuration and tagging on the AWS firewall resource.
- On you VPC Dashboard go to: Network Firewall >> Firewalls and click on create.


- We choose the VPC where we want our Firewall to inspect the traffic.
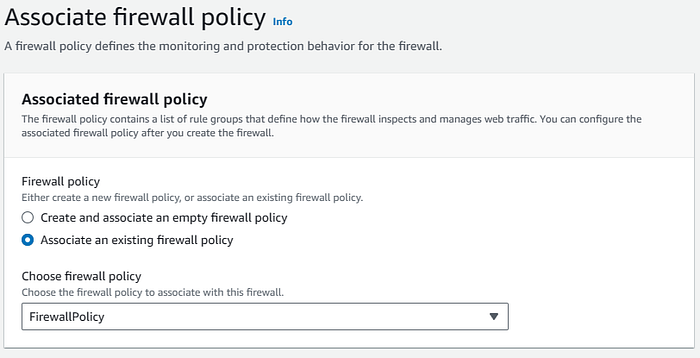
- We associate the Firewall Policy created on the previous step with our Network Firewall.
Note: Once the firewall creation is completed, go to the details and take note of the Endpoint ID. We will use that value later.

Loggin
Network Firewall generates logs for stateful rule groups. You can configure different destinations for different log types.
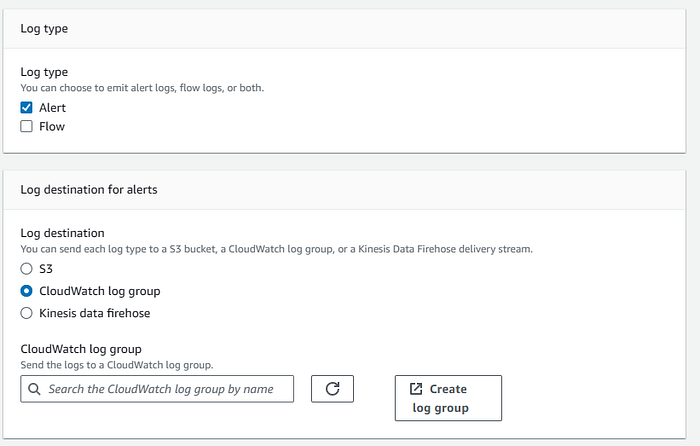
Note: You can record alert logs and flow logs from your Network Firewall stateful engine.
Firstly, alert logs report traffic that matches your stateful rules when an action sends an alert. A stateful rule generates alerts for the rule actions DROP, ALERT, and REJECT.
Meanwhile, flow logs capture standard network traffic flow. Each flow log record tracks the network flow for a specific standard stateless rule group.
Finally, keep any other value as default and proceed all the way to “Create Firewall”.
Step 4: Routing Configuration
Up to this point, we have created:
- Subnet for our Firewall
- Rule Groups (Stateful and Stateless)
- Firewall Policy
- Network Firewall
Before you begin testing out your firewall rules, you need to adjust routing to send traffic through the firewall.
We need to create two new Route Tables:
Firewall subnet route table.
Internet gateway (IGW) ingress route table.
Internet Gateway Route Table
- On your VPC Dashboard go to: Route Tables >> Create Route Table
When creating this Route Table, make sure to select the right VPC. On the Edit edge associations section, click on edit and select the Internet gateway.
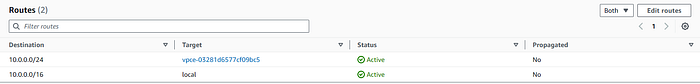
Now we need to create a route entry that will forward the incoming traffic to the Firewall.
- For Destination, enter use the CIDR of your public subnet network. In our lab the address is: 10.0.0.0/24
- For Target, select Gateway Load Balancer Endpoint and search for the VPC firewall endpoint that starts with vpce-.
Note: Use the Network Firewall Endpoint ID from step 3.
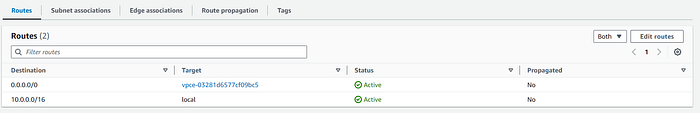
Firewall route table
We will create a new route table for our firewall and will direct all the outgoing traffic (0.0.0.0/0) to the internet gateway.
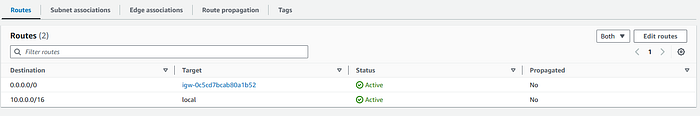
We associate this route table with the FirewallSubnet created on step 1.
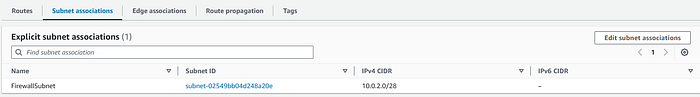
Finally, we configure our Public Route table (part of the pre-requirement) to forward the outgoing traffic to the Firewall.
Note: Use the Network Firewall Endpoint ID from step 3.
At this point we should have the following three route tables:
- Public Route table
- Ingress Route table
- Firewall Route table
Step 5: Testing
We will verify network connectivity between the EC2 instances and the internet to evaluate the firewall’s ability to block or allow traffic based on your defined rules.
Connecting to our EC2 via CLI we can perform the following:
- Using “curl” we will check connectivity with the domains listed on the DomainList Rule Group
- Using “ping” we will test the Stateful Standard Rule Group created for ICMP traffic.
At this point both Rule Groups are configured as Allow or Pass, then we should have the following behavior:
curl www.example.com
<!doctype html>
<html>
<head>
<title>Example Domain</title>
<meta charset="utf-8" />
<meta http-equiv="Content-type" content="text/html; charset=utf-8" />
<meta name="viewport" content="width=device-width, initial-scale=1" />
<style type="text/css">
body {
background-color: #f0f0f2;
margin: 0;
padding: 0;
font-family: -apple-system, system-ui, BlinkMacSystemFont, "Segoe UI", "Open Sans", "Helvetica Neue", Helvetica, Arial, sans-serif;
}
div {
width: 600px;
margin: 5em auto;
padding: 2em;
background-color: #fdfdff;
border-radius: 0.5em;
box-shadow: 2px 3px 7px 2px rgba(0,0,0,0.02);
}
a:link, a:visited {
color: #38488f;
text-decoration: none;
}
@media (max-width: 700px) {
div {
margin: 0 auto;
width: auto;
}
}
</style>
</head>
<body>
<div>
<h1>Example Domain</h1>
<p>This domain is for use in illustrative examples in documents. You may use this
domain in literature without prior coordination or asking for permission.</p>
<p><a href="https://www.codezaza.com/domains/example">More information...</a></p>
</div>
</body>
</html>
ping 8.8.8.8
PING 8.8.8.8 (8.8.8.8) 56(84) bytes of data.
64 bytes from 8.8.8.8: icmp_seq=1 ttl=116 time=10.0 ms
64 bytes from 8.8.8.8: icmp_seq=2 ttl=116 time=11.2 ms
64 bytes from 8.8.8.8: icmp_seq=3 ttl=116 time=11.0 ms
64 bytes from 8.8.8.8: icmp_seq=4 ttl=116 time=10.5 ms
^C
--- 8.8.8.8 ping statistics ---
4 packets transmitted, 4 received, 0% packet loss, time 3004ms
rtt min/avg/max/mdev = 10.015/10.726/11.292/0.489 msEverything seems to be working as expected. Now, we will modify the action on each of the Rule Groups to Deny or Drop.
curl www.example.com --max-time
— max-time 5 tell the curl command to only try for 5 connections.
As we can see, we are not able to connect to www.example.com
PING 8.8.8.8 (8.8.8.8) 56(84) bytes of data.
--- 8.8.8.8 ping statistics ---
5 packets transmitted, 0 received, 100% packet loss, time 4088ms
The same result when using ping.
This confirms that the Stateful Rule Groups are working as expected and traffic is denied.
AWS Network Traffic Flow Details
AWS Network Firewall inspects your network traffic without performing network address translation (NAT). This transparent inspection keeps the source and destination IP addresses intact, so the traffic’s original structure remains unchanged.
When a packet arrives at the firewall, the inspection process begins. The firewall routes the packet through the rules engine, examines it, and then either allows or blocks it according to the security rules you defined.
Moreover, AWS Network Firewall integrates seamlessly with your VPC’s routing setup. By using VPC route tables and the Gateway Load Balancer, it ensures traffic flows through the firewall without disrupting the rest of your network.red and secure
AWS Network Firewall Deployment Models
AWS Network Firewall (ANF) offers advanced security features like deep packet inspection (DPI), application protocol detection, domain filtering, and intrusion prevention. It secures your network by examining both incoming and outgoing traffic. You can apply a wide range of security rules to protect your VPCs.
Let’s explore the different deployment models:
1. Distributed Deployment Model
In this model, each VPC gets its own firewall. Think of it as giving every network area its own security guard. Traffic entering or leaving each VPC passes through its dedicated firewall, allowing you to enforce customized security rules for each VPC independently.
2. Centralized Deployment Model
Here, you deploy the firewall in a single location, often called a central inspection VPC. This setup inspects traffic between VPCs or between your cloud network and external sources, such as the internet. It simplifies rule management and centralizes monitoring.
3. Combined Deployment Model
This hybrid model combines distributed and centralized approaches. You deploy AWS Network Firewall in a central inspection VPC to manage VPC-to-VPC (east-west) traffic and some external traffic (north-south), like outbound internet or on-premises connections. Additionally, VPCs that require direct internet access get their own dedicated ANF endpoints to inspect incoming traffic effectively.
Features of AWS Network Firewall
Here are some of the standout features that make AWS Network Firewall a powerful tool for cloud security:
1. Deep Packet Inspection (DPI)
This feature inspects network traffic at a very detailed level to detect and block harmful content such as malware or unauthorized access attempts.
2. Stateful and Stateless Rule Engines
AWS Network Firewall lets you define different types of rules. Stateful rules look at the state of network connections (like whether a session is ongoing), while stateless rules are simpler and just check the packet content.
3. Intrusion Prevention System (IPS)
AWS Network Firewall can automatically detect and block threats like DDoS attacks, ensuring your network is protected without you having to do anything.
4. Scalable and Highly Available
AWS Network Firewall scales automatically to match the demands of your network, making sure you always have the resources you need to handle traffic. It also works across multiple Availability Zones (AZs), ensuring high availability and resilience.
5. Integration with AWS Services
AWS Network Firewall works well with other AWS services, such as VPC, CloudWatch, and Transit Gateway, providing a unified approach to security management.
Benefits of AWS Network Firewall
1. Fully Managed Service
AWS handles all aspects of the firewall, including scaling, updates, and maintenance. You don’t need to worry about managing infrastructure, allowing you to focus on securing your applications.
2. Scalable & Flexible
The firewall automatically adjusts to your network traffic demands. Whether you run a small app or a large enterprise system, it provides consistent protection without manual intervention.
3. Customizable Rules
You can define security rules that match your specific requirements. This gives you full control over which traffic is allowed or blocked, tailoring protection to your network’s needs.
4. Centralized Management
AWS Network Firewall enables you to manage security policies across multiple VPCs from a single location. This simplifies policy enforcement and ensures consistency across your cloud environment.
5. Seamless AWS Integration
It integrates smoothly with services like VPC, Transit Gateway, and Security Hub, providing a unified approach to cloud security. This integration reduces complexity and improves monitoring across your AWS environment.
6. Compliance & Auditing
The firewall helps you meet regulatory standards such as GDPR, HIPAA, and PCI-DSS. It also generates detailed audit logs, giving you transparency and helping with compliance reporting.
7. Cost-Effective
You pay only for the traffic that passes through the firewall. This usage-based pricing makes it more affordable compared to traditional hardware firewalls, especially for dynamic cloud workloads.
8. Easy Setup
AWS Network Firewall is simple to set up. It integrates seamlessly into your existing AWS environment, allowing you to deploy protection quickly without complex configuration..
Use Cases of AWS Network Firewall
1. Securing Virtual Private Clouds (VPCs)
AWS Network Firewall is perfect for protecting your VPCs by controlling the traffic between subnets and ensuring that only trusted sources can access your network. It helps you enforce security across multiple VPCs from a central point.
2. Preventing Data Exfiltration
You can configure the firewall to block unauthorized outgoing traffic, which helps prevent sensitive data from being leaked outside your network and keeps your data secure.
3. Network Segmentation
AWS Network Firewall lets you break your network into different zones and apply stricter security measures where needed. This minimizes exposure to security threats and isolates critical workloads from less important ones.
4. Compliance with Regulations
For industries like healthcare or finance that require strict security standards, AWS Network Firewall helps you stay compliant with regulations like HIPAA, PCI-DSS, and GDPR by enforcing network rules and keeping detailed logs for audits.
5. Securing Hybrid Cloud Environments
If you have both on-premises systems and AWS cloud resources, AWS Network Firewall can secure the communication between the two, ensuring consistent security across both environments.
6. Defense Against DDoS and Other Attacks
AWS Network Firewall adds an extra layer of protection against distributed denial-of-service (DDoS) attacks and other malicious threats, helping block harmful traffic before it reaches your cloud services.
7. Centralized Security Management
For businesses with multiple VPCs in different regions, AWS Network Firewall allows you to manage security policies from a central location, ensuring all traffic is properly controlled and consistent.
8. Application-Specific Traffic Control
You can create custom rules to allow or block specific types of traffic based on the application, ensuring that only approved web traffic or other types of data flow through your network.
9. Securing Microservices
In a microservices architecture, where services communicate over a network, AWS Network Firewall helps secure service-to-service communication by enforcing strict rules for traffic between them.
AWS Network Firewall Pricing
The pricing for AWS Network Firewall depends on several factors, including the amount of traffic processed, deployment configuration, and additional features you use. Here’s a breakdown:
1. Traffic Processing
You’re charged based on the amount of traffic that passes through the firewall. This is measured in gigabytes (GB) and applies to all traffic inspected, whether it’s coming in or going out.
2. Advanced Traffic Inspection
If you enable features like TLS inspection to analyze encrypted traffic, there will be additional charges depending on the volume of traffic processed and the regions where it’s used.
3. NAT Gateway Discount
If you’re using a NAT Gateway with AWS Network Firewall, there’s no extra cost for data processed through the gateway when it’s set up correctly. This can help lower overall costs.
4. Firewall Endpoint Charges
You will be charged for the firewall endpoints you deploy in your VPC. These endpoints are powered by AWS Gateway Load Balancer, and you pay based on how many endpoints are running and how long they are used.
5. Data Transfer Charges
Standard AWS data transfer fees apply to any traffic processed by the firewall, especially when transferring data between different AWS services or regions.
The pricing is flexible, meaning you only pay for what you use. If you deploy multiple firewalls in different regions or availability zones, the costs will adjust based on your specific setup and traffic volume.
Conclusion
AWS Network Firewall offers a comprehensive, scalable, and cost-effective solution to secure your cloud infrastructure. Whether you’re a small business or an enterprise, AWS Network Firewall provides the tools you need to safeguard your network from malicious traffic, ensure compliance, and maintain high availability. Its deep packet inspection, customizable rules, and seamless integration with other AWS services make it a critical part of any cloud security strategy. With flexible deployment options and an easy-to-manage pricing model, it provides a robust defense against cyber threats while scaling with your cloud environment’s needs.