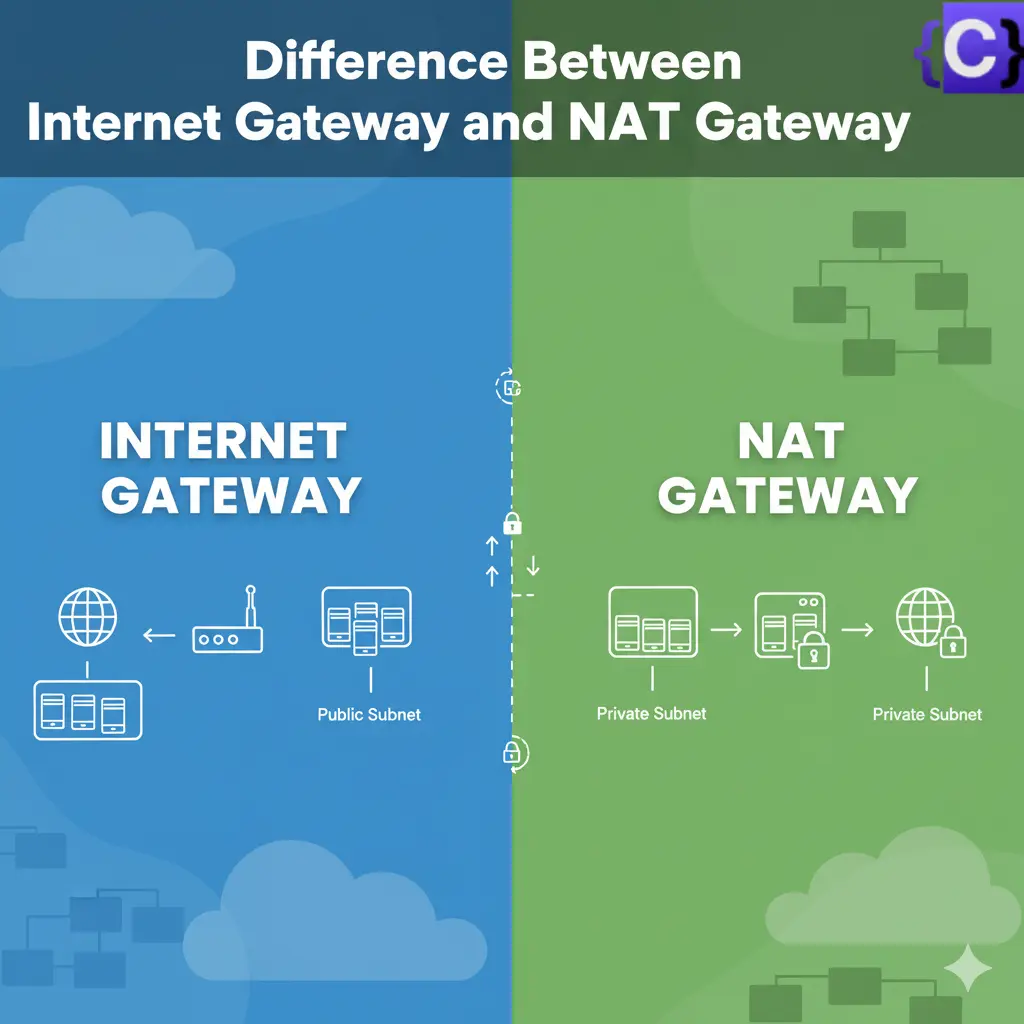
Both the AWS Internet Gateway and NAT Gateway are essential networking resources that ensure your VPC resources, like EC2 instances, can communicate with the public internet. The main difference between the two is that the Internet Gateway enables both inbound and outbound communication with the internet, whereas the NAT Gateway only plays a role in outbound communication. Let’s now take a closer look at the differences between these two and when to use each of these resources.
Internet Gateway
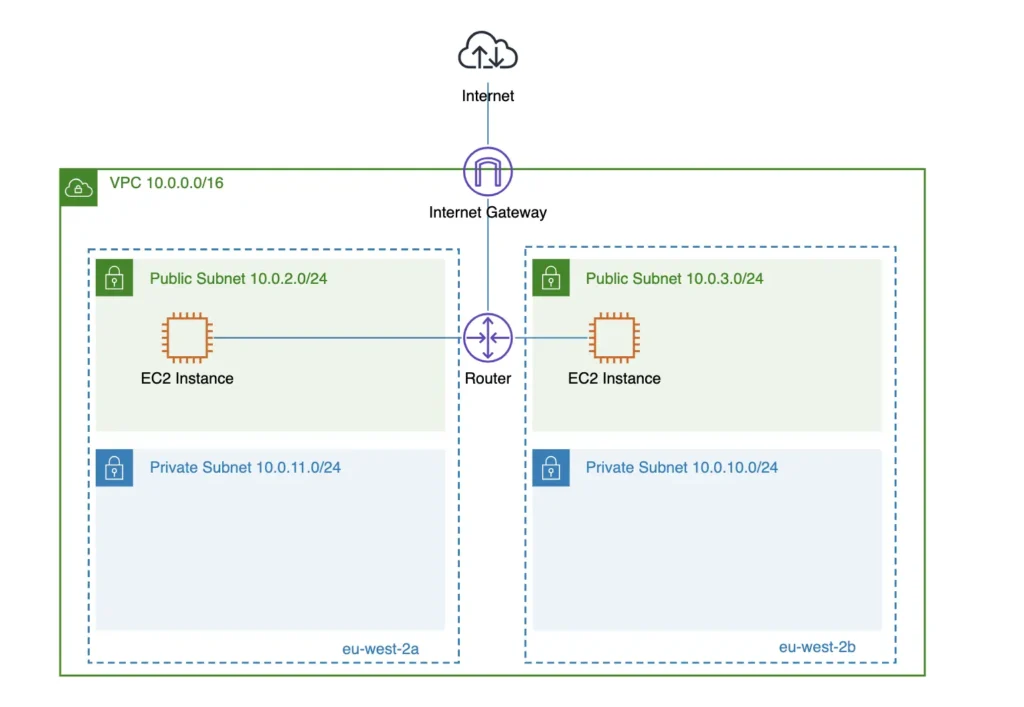
An Internet Gateway (IGW) enables resources in a VPC to communicate with the internet. It is horizontally scaled, redundant, and highly available. Think of it as a virtual router that connects your VPC to the internet and supports bidirectional traffic flow.
The IGW establishes a direct connection between a VPC and the internet. To use it, your VPC must have at least one public subnet. Instances inside that subnet also need public IP addresses to send and receive traffic.
The Internet Gateway works by translating private IP addresses in the VPC to public IP addresses. This translation allows external systems to reach your resources. For example, if you host a web server in your VPC, you can attach an IGW to make the server accessible from the internet.
AWS internet gateway is a highly available VPC component that provides internet access to your VPC resources (e.g., EC2 instances, Load Balancers, NAT gateways), supporting both inbound and outbound traffic for instances with public IP addresses.
As the internet gateway is fully managed by AWS, the only optional configuration during creation is the name tag:
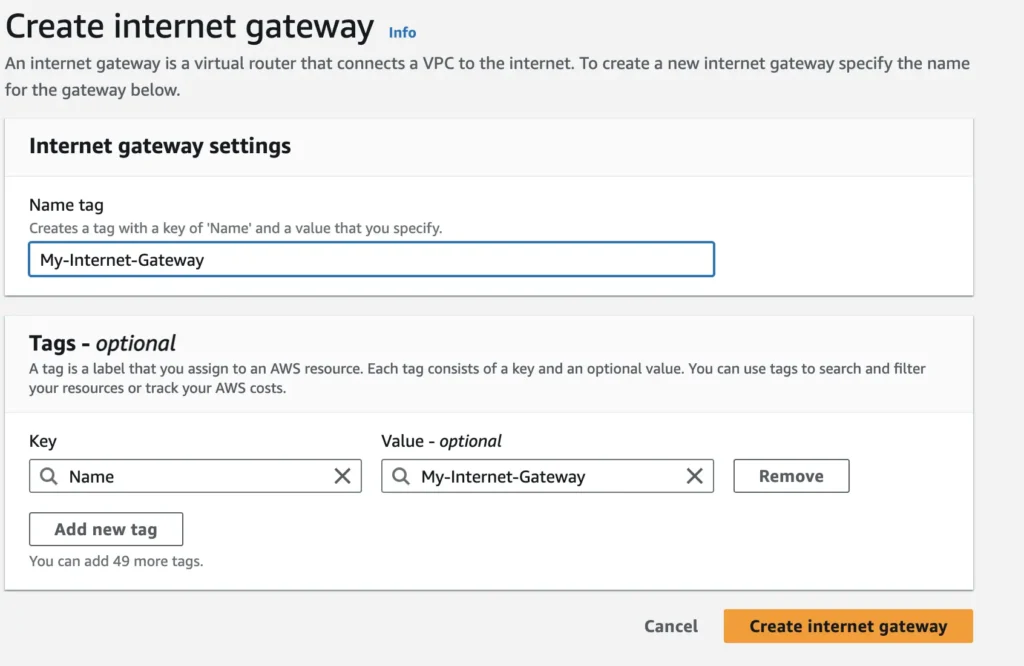
In order to start to use internet gateway you have to do the following:
- Attach internet gateway to VPC
- Add route
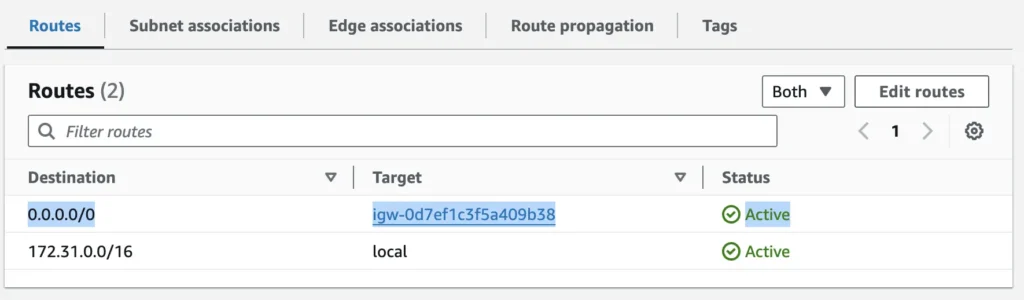
0.0.0.0/0 - igw-xxxxxto your route table for public subnets to route outbound traffic to internet gateway. Keep in mind that only instances that have public IPv4 or IPv6 address can send outbound traffic to internet gateway. - In order to control inbound or outbound traffic to your instances specific security group rules and network access control lists should be used.
NAT Gateway
A NAT Gateway allows instances in a private subnet to connect to the internet or other AWS services. It blocks inbound connections from the internet, keeping those instances secure.
The NAT Gateway works by translating private IP addresses into public IP addresses. When an instance in a private subnet sends traffic, it routes the request to the NAT Gateway. The gateway then replaces the private IP with a public IP and forwards the traffic to the internet.
You typically use a NAT Gateway when private resources need outbound internet access but must remain unreachable from the internet. For example, a database server inside a private subnet can use a NAT Gateway to download software updates or fetch data from an external source.
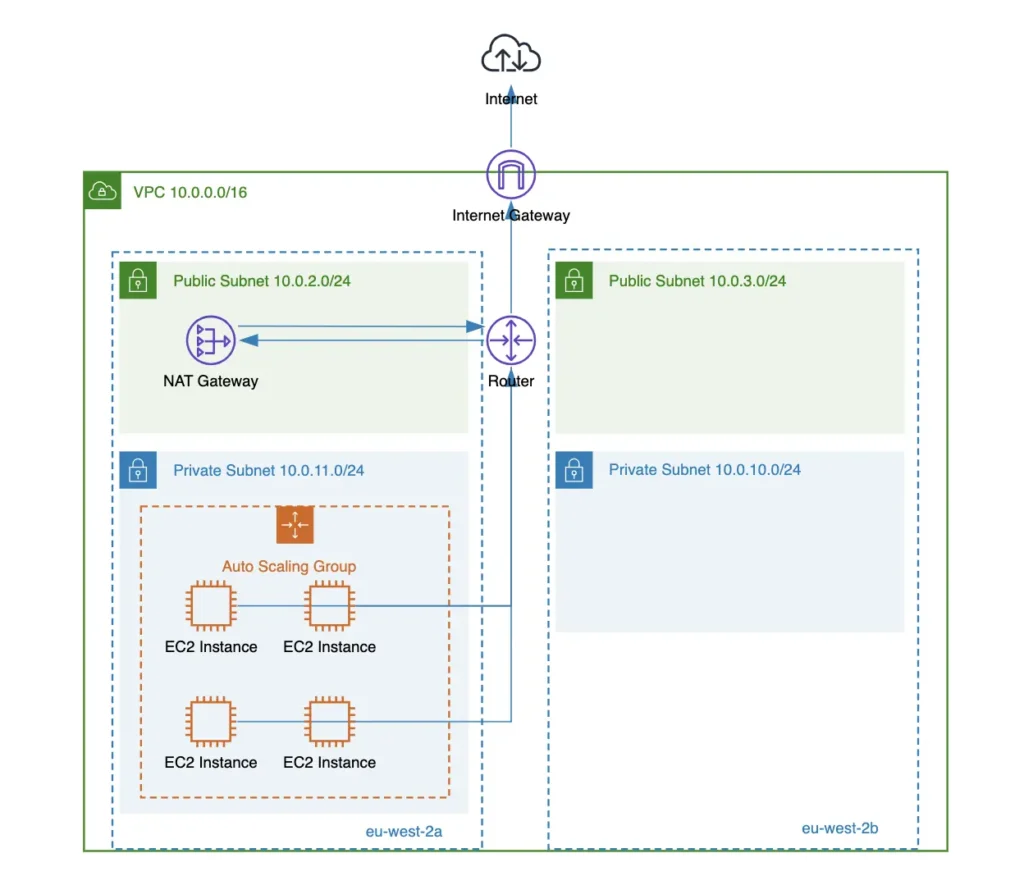
AWS NAT gateway is an AWS managed network address translation (NAT) service mainly used to allow instances in private subnets to connect to the public internet while preventing unsolicited inbound connections from the internet. You can still use public AWS load balancers which can route traffic from the internet to private instances, but this, of course, would be your controlled inbound traffic.
There are two types of NAT gateways
1. Public NAT Gateway
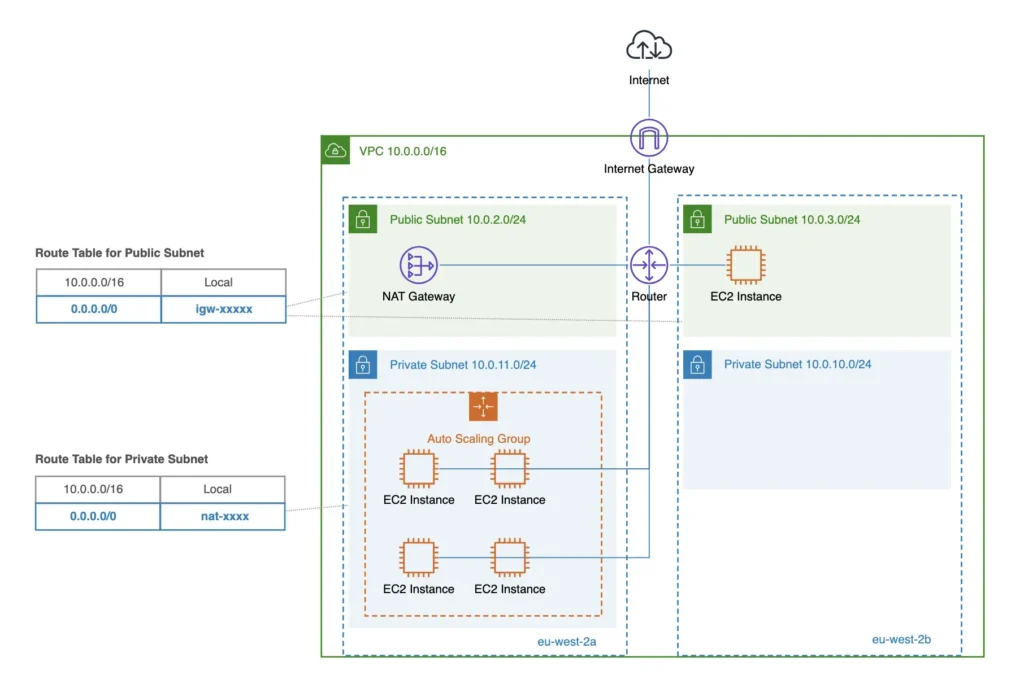
A public NAT gateway allows instances in private subnets to connect to the internet. When creating this gateway, you must assign an Elastic IP address. It should always be deployed in a public subnet that has a route to an Internet Gateway. If you mistakenly place a public NAT gateway in a private subnet, it will fail to route traffic to the internet.
2. Private NAT Gateway
A private NAT gateway enables private instances to connect to other VPCs or on-premises networks. You should carefully review your network design before using it, because it adds extra cost and latency. Often, routing traffic directly from an EC2 instance to a VPC peering connection or VPN gateway is faster and cheaper.
You should use a private NAT gateway only when the destination, such as an on-premises network, allows traffic from a specific or limited IP range. In this setup, the traffic passes through the NAT gateway and uses its private IP address as the source.
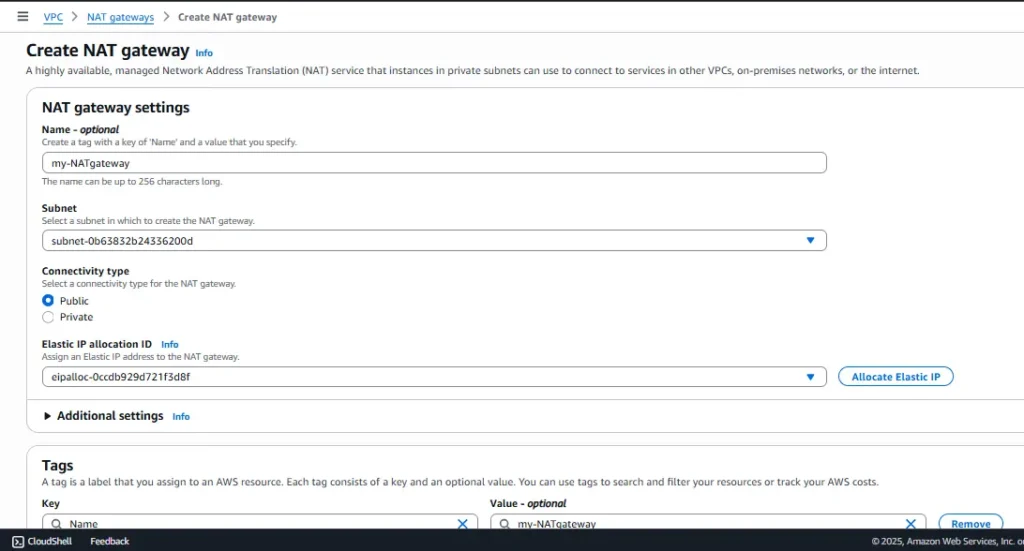
To start using a public NAT gateway after creating it:
- Add the route
0.0.0.0/0 - nat-xxxxxto your route table for private subnets to allow instances to route traffic through the NAT gateway. - To control outbound traffic from your instances, specific security group rules and network access control lists (NACLs) should be applied.
What are the Differences Between Internet Gateway and NAT Gateway?
There are differences between the internet gateway and NAT gateway, which we will now describe in more detail. This will help us better understand when to use each of these AWS networking resources.
Purpose
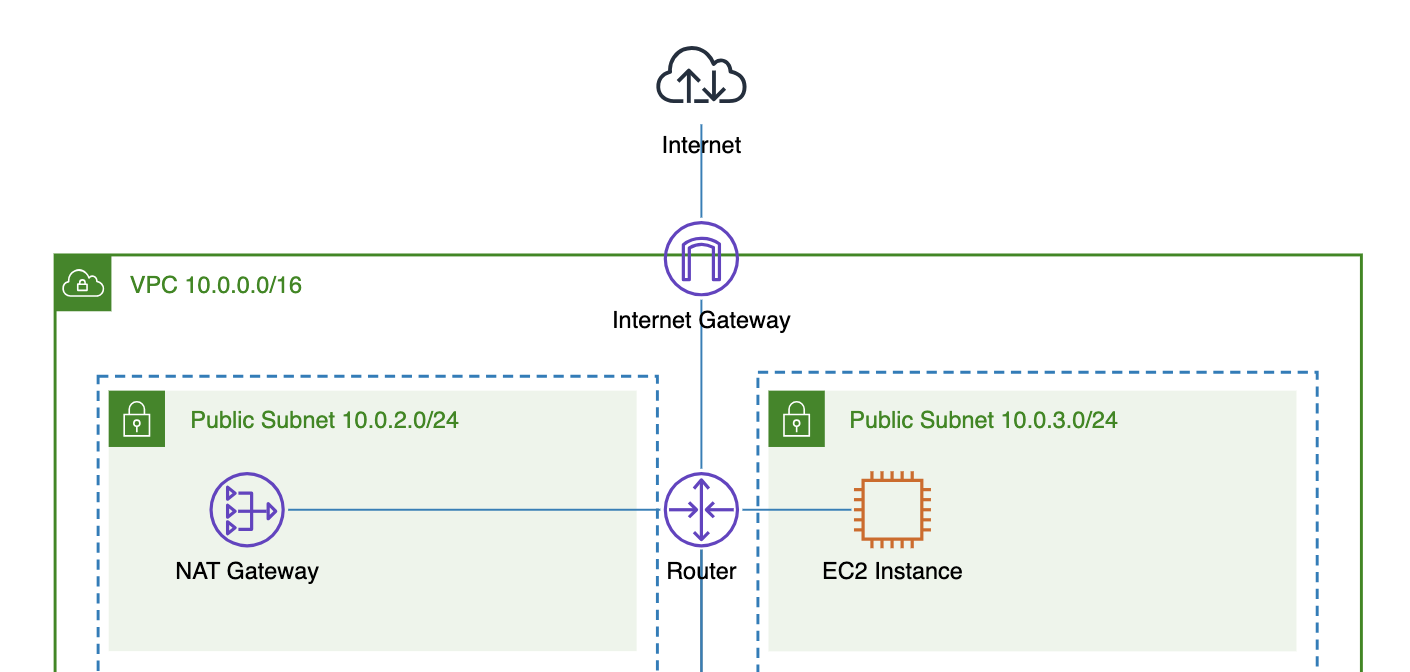
The AWS internet gateway is the main bridge between your VPC and the internet. If an internet gateway is not attached to the VPC, all deployed resources (e.g., EC2 instances, load balancers, Lambda functions, etc.) will not be accessible from the public internet, and vice versa—they will not be able to access any public internet resources either.
However, the NAT gateway acts only as an intermediary for outbound traffic from your private instances, translating private IP addresses to a common public IP address (or a private IP address in the case of a private NAT gateway) and blocking any unsolicited inbound traffic.
Dependency
I have often heard and seen the misleading assumption that the NAT gateway communicates directly with the public internet, but that’s not true. When the NAT gateway receives traffic from your private instances (e.g., EC2 instances), this traffic must be routed to an internet gateway in order to reach the public internet.
Without a route to the internet gateway, traffic stays inside the VPC. The public NAT gateway uses its Elastic IP (public IP address) as the source IP only when it connects to an internet gateway in the same VPC.
You can also route traffic from the NAT gateway to a VPN gateway (for example, to reach an on-premises network) or to a transit gateway (to reach other VPCs). However, this traffic still cannot directly reach the public internet because it originates from the private IP address of the NAT gateway.
In contrast, an internet gateway works independently and does not require a NAT gateway to function.
Traffic Direction
The AWS Internet Gateway supports both inbound and outbound traffic between VPC resources with public IP addresses (such as EC2 instances or load balancers) and the public internet.
If an EC2 instance has a public IP, the subnet has a route to the Internet Gateway (for example, 0.0.0.0/0 → igw-xxxxx), and the gateway is attached to the VPC, then the instance becomes accessible. Inbound traffic depends on the security group rules. The instance can also send outbound requests to the public internet.
In contrast, the NAT Gateway supports only outbound traffic initiated by VPC resources such as EC2 instances or Lambda functions. Requests that start from the public internet never reach private VPC resources that rely on a NAT Gateway for outbound communication.
Availability
The AWS Internet Gateway provides high availability by default. If one Availability Zone goes down, it can still route traffic through other active zones in your VPC.
With a NAT Gateway, the setup is different. When you deploy resources across multiple Availability Zones (for example, EC2 instances in different AZs), you must create a NAT Gateway in each zone. This setup ensures that private resources do not lose internet access if one zone becomes unavailable.

IPv4/IPv6 vs IPv4 only
Internet gateway supports both IPv4 and IPv6 traffic.
NAT gateway only supports IPv4.
To allow outbound-only IPv6 traffic from instances to communicate with the public internet, you can use an egress-only internet gateway. The egress-only gateway is a highly available VPC component designed specifically for IPv6 traffic.
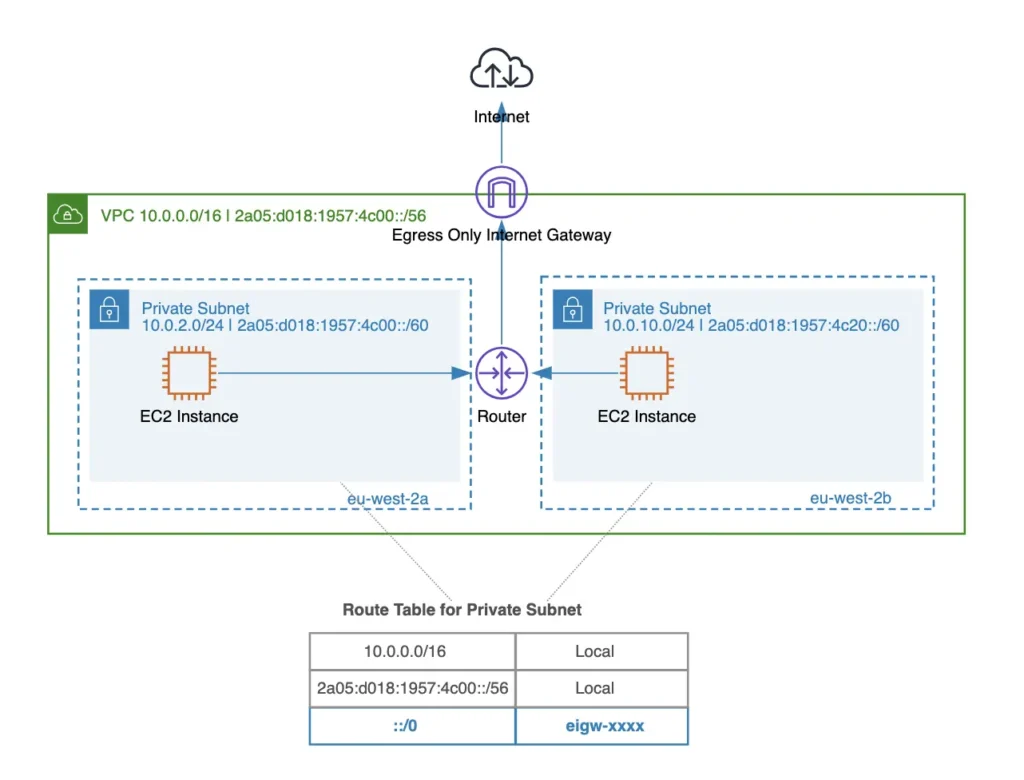
Sharing Across VPCs
An Internet Gateway cannot be shared across multiple VPCs. Each VPC requires its own dedicated Internet Gateway if you want direct internet access.
A NAT Gateway, however, offers more flexibility. You can indirectly share it across VPCs by using Transit Gateway attachments or VPC peering connections. In this setup, one VPC acts as a central egress VPC. The NAT Gateways in this egress VPC handle internet-bound traffic for multiple spoke VPCs.
This design is often called the centralized egress pattern. It helps reduce operational overhead and costs by avoiding the need to deploy separate NAT Gateways in every VPC. All outbound traffic from spoke VPCs is routed through the central egress VPC. From there, the NAT Gateway translates private IPs into public IPs and forwards the requests to the internet.
However, this architecture also introduces extra hops in the network path, which may add latency. You should carefully evaluate your workload requirements, such as throughput, latency tolerance, and security rules, before adopting a shared NAT Gateway design.
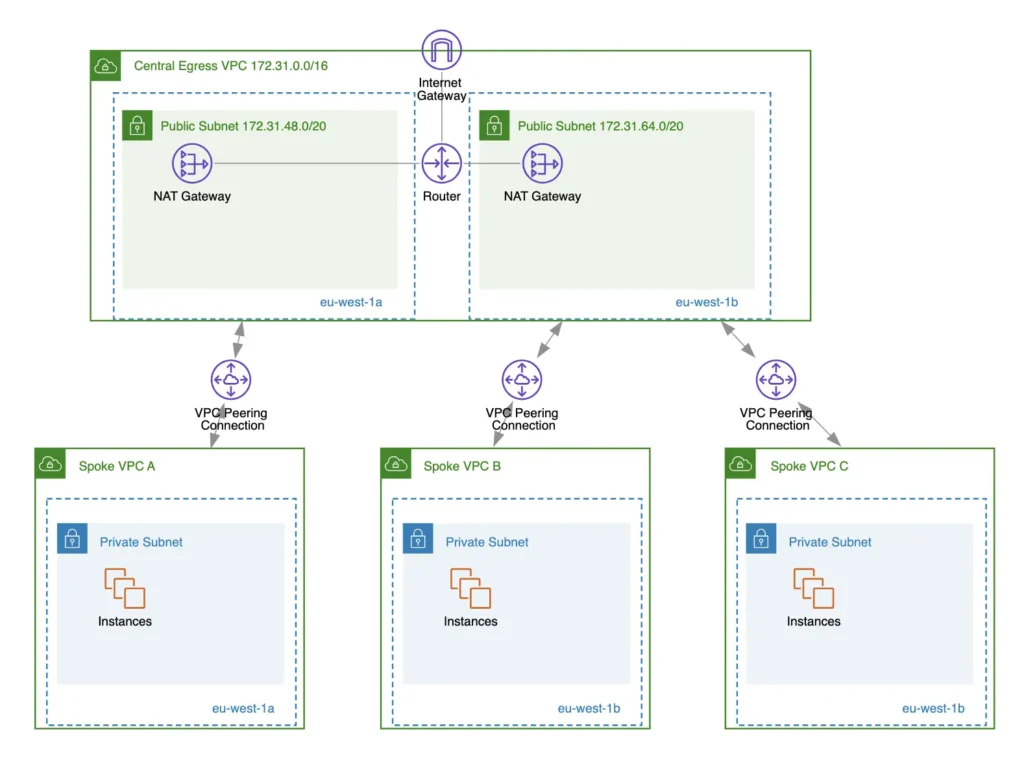
This can provide several benefits, such as:
- Reduced NAT gateway costs: We don’t have to provision NAT gateways in every spoke VPC.
- Simplified management: All outbound internet access goes through one specific VPC, allowing us to implement security policies, logging, and monitoring in one place.
However, before using this AWS network architecture, please consider all the additional costs associated with VPC peering or transit gateway attachment usage
Cost
For the AWS internet gateway, there are no additional costs associated with its use; only standard data transfer costs apply.
For the NAT Gateway, in addition to standard data transfer costs:
- Price per NAT gateway: $0.045 per hour.
- Data processing charge: $0.045 per GB.
Here you can clearly see that using one NAT Gateway for a whole month (30 days) and processing 100 GB of data would cost around $36.90 ($32.40 for hourly usage + $4.50 for data processing).
When to Use Each
Use an AWS Internet Gateway whenever your application requires public inbound and outbound traffic. This means your application is accessible from the internet. Common examples include:
- Web servers that serve public websites.
- API endpoints that need to respond to requests from external clients.
- Public-facing services such as load balancers or content delivery systems.
The Internet Gateway ensures that instances with public IP addresses can send and receive traffic from the internet. It also handles network address translation (NAT) for these public IPs automatically, making communication seamless and highly available across multiple Availability Zones.
Use a NAT Gateway when you want private VPC instances to access the internet without exposing them to inbound connections. Examples include:
- EC2 instances in private subnets that need software updates.
- Lambda functions or application servers that require external API calls.
- Database servers that need to fetch external data or connect to external services securely.
By combining a NAT Gateway with an Internet Gateway, you can create a secure and scalable architecture:
This setup prevents unsolicited inbound traffic from reaching private resources, enhancing security.
The Internet Gateway handles public traffic and acts as the primary connection to the internet.
Private instances route outbound traffic through the NAT Gateway, which translates their private IPs to public IPs for internet access.
Conclusion
Internet Gateways and NAT Gateways serve distinct but complementary roles in AWS networking. An Internet Gateway enables bidirectional traffic between public VPC resources and the internet, making applications publicly accessible. In contrast, a NAT Gateway allows private VPC resources to initiate outbound connections to the internet while keeping them protected from unsolicited inbound traffic.
Choosing the right gateway depends on your application’s requirements: use an Internet Gateway for public-facing services and a NAT Gateway for private resources that need secure outbound internet access. By combining both strategically, you can build a scalable, secure, and highly available VPC architecture that meets both accessibility and security needs.